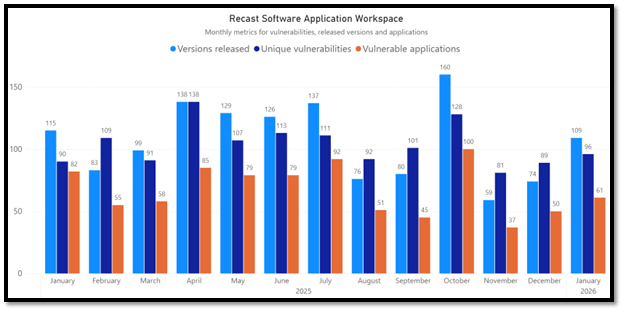
January picked up again after December’s slowdown. We logged 96 unique vulnerabilities across 61 applications, and remediation work drove more than a thousand version updates. Activity was clearly higher than in the previous month, with both findings and patches trending upward.
Notable vulnerabilities in January 2026 third-party patches
I have good news. There are no vulnerabilities with known exploits and none of the vulnerabilities have an elevated EPSS rating. This month we will focus on vulnerabilities with the highest CVSS rating.
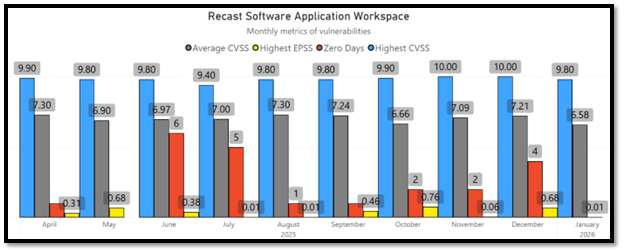
First, CVE‑2025‑15467 is a critical OpenSSL vulnerability involving a stack buffer overflow when processing CMS AuthEnvelopedData messages. An attacker can trigger the overflow before authentication or tag verification occurs, meaning the issue can be exploited without valid key material. The impact ranges from denial of service to possible remote code execution, depending on compilation hardening. The vulnerability affects OpenSSL versions across several major Linux distributions and vendor builds. With a CVSS score of 9.8, this should be treated as a high‑priority patch for any environment using OpenSSL 3.x. In the Setup Store application catalog, it affects OpenSSL by Shining Light Productions. More information about this vulnerability can be found in OpenSSL’s Security Advisory. The following versions will patch the vulnerability:
- OpenSSL 3.4.4
- OpenSSL Light 3.4.4
CVE–2025–66471 is a vulnerability in the Python urllib3 library tied to how compressed data is decompressed. A malicious server can get excessive CPU and memory usage, creating a denial‑of‑service condition. It affects urllib3 versions 1.0 through 2.5.0 and impacts a wide range of Linux distributions and cloud‑native ecosystems that embed urllib3 by default. With a CVSS score of 8.9, organizations should update to urllib3 2.6.0 or vendor‑provided patched builds. Full details can be found in the urllib3 release documentation and distribution advisories. It affects Microsoft Azure CLI, and it is patched in version 2.82.0.
A related issue, CVE–2025–66418, also impacts urllib3 and allows a malicious server to create an effectively unbounded decompression chain, leading to resource exhaustion. Like the previous vulnerability, this affects a broad set of Python‑based systems, including those embedded in orchestrators, automation tools, and cloud workflows. CVSS is 8.9, and the recommended remediation is the same: upgrade to urllib3 2.6.0. Additional information is available through urllib3 maintainers and security bulletins. The vulnerability also affects Microsoft Azure CLI.
CVE–2026–0885 is a use‑after‑free vulnerability in Mozilla Firefox and Thunderbird’s JavaScript garbage collector. A crafted webpage can trigger arbitrary code execution or denial of service. Affected versions include Firefox before 147, ESR before 140.7, and Thunderbird before the same thresholds. With a CVSS score of 8.8, this warrants timely patching, particularly for organizations with high browser exposure. More details can be found in Mozilla’s security advisories and release notes.
Browser security updates in January 2026
Major browsers, including Google Chrome, Microsoft Edge, Brave, Mozilla Firefox (including ESR versions), Opera One, Vivaldi, and others received numerous security updates addressing various vulnerabilities.
| Browser | Vulnerabilities | Updates |
| Google Chrome | 13 | 4 |
| Microsoft Edge | 14 | 4 |
| Brave Browser | 13 | 4 |
| Mozilla Firefox | 18 | 2 |
| Mozilla Firefox 115 | 5 | 1 |
| Mozilla Firefox 140 | 14 | 2 |
| Opera One | 1 | 1 |
| Vivaldi | 1 | 1 |
| Waterfox | 13 | 1 |
Microsoft product updates included in January 2026 third-party patches
In addition to Edge, Microsoft issued security updates for several other products:
| Microsoft 365 Apps |
| Microsoft Edge for Business |
| Microsoft Edge Beta |
| Microsoft Azure Kubelogin |
| Microsoft Azure CLI |
Detailed list of January 2026 third-party patches
For a complete list of applications, versions, and the number of remediated vulnerabilities, see the table below generated using Application Workspace data.
| Product Name | Version Name | Vulnerabilities remediated |
| Akeo Consulting Rufus | 4.12 | 1 |
| Amazon Corretto JDK | 25.0.2.10.1 | 4 |
| Amazon Corretto JDK 11 | 11.0.30.7.1 | 4 |
| Amazon Corretto JDK 17 | 17.0.18.8.1 | 4 |
| Amazon Corretto JDK 21 | 21.0.10.7.1 | 4 |
| Amazon Corretto JDK 8 | 8.482.08.1 | 4 |
| Amazon Corretto JRE 8 | 8.482.08.1 | 4 |
| Brave Browser | 1.86.139 | 10 |
| Brave Browser | 1.86.146 | 1 |
| Brave Browser | 1.86.142 | 1 |
| Brave Browser | 1.85.120 | 1 |
| Burp Suite Community Edition | 2025.12.3 | 1 |
| Burp Suite Community Edition | 2026.1 | 1 |
| Burp Suite Community Edition | 2026.1.2 | 1 |
| Burp Suite Community Edition | 2026.1.1 | 10 |
| Burp Suite Professional Edition | 2025.12.3 | 1 |
| Burp Suite Professional Edition | 2026.1 | 1 |
| Burp Suite Professional Edition | 2026.1.2 | 1 |
| Burp Suite Professional Edition | 2026.1.1 | 10 |
| Chef Infra Client | 18.9.4 | 1 |
| Chef Infra Client for Windows 10 | 18.9.4 | 1 |
| Chef Infra Client for Windows 11 | 18.9.4 | 1 |
| Chef Infra Client for Windows Server 2016 | 18.9.4 | 1 |
| Chef Infra Client for Windows Server 2019 | 18.9.4 | 1 |
| Chef Infra Client for Windows Server 2022 | 18.9.4 | 1 |
| Chef Infra Client for Windows Server 2025 | 18.9.4 | 1 |
| Google Chrome | 144.0.7559.59 | 10 |
| Google Chrome | 144.0.7559.60 | 10 |
| Google Chrome | 144.0.7559.109 | 1 |
| Google Chrome | 144.0.7559.110 | 1 |
| Google Chrome | 144.0.7559.96 | 1 |
| Google Chrome | 144.0.7559.97 | 1 |
| Google Chrome | 143.0.7499.193 | 1 |
| Google Chrome | 143.0.7499.192 | 1 |
| Google Chrome for Business | 144.0.7559.60 | 10 |
| Google Chrome for Business | 144.0.7559.110 | 1 |
| Google Chrome for Business | 144.0.7559.97 | 1 |
| Google Chrome for Business | 143.0.7499.193 | 1 |
| Google Chrome for Education | 144.0.7559.60 | 10 |
| Google Chrome for Education | 144.0.7559.110 | 1 |
| Google Chrome for Education | 144.0.7559.97 | 1 |
| Google Chrome for Education | 143.0.7499.193 | 1 |
| Google Go Programming Language | 1.25.6 | 6 |
| Google Go Programming Language | 1.24.12 | 6 |
| Grafana k6 | 1.5.0 | 1 |
| Liberica JDK | 25.0.2.12 | 11 |
| Liberica JDK | 8.0.482.10 | 11 |
| Liberica JDK | 11.0.30.9 | 11 |
| Liberica JDK | 17.0.18.10 | 11 |
| Liberica JDK Lite | 25.0.2.12 | 11 |
| Liberica JDK Lite | 11.0.30.9 | 11 |
| Liberica JDK Lite | 21.0.10.10 | 11 |
| Liberica JDK Lite | 8.0.482.10 | 11 |
| Liberica JRE | 25.0.2.12 | 11 |
| Liberica JRE | 21.0.10.10 | 11 |
| Liberica JRE | 8.0.482.10 | 11 |
| Liberica JRE | 11.0.30.9 | 11 |
| Mendix 9 | 9.24.41.90173 | 5 |
| Microsoft 365 Apps | 2508 (Build 16.0.19127.20484) | 11 |
| Microsoft 365 Apps | 2508 (Build 16.0.19127.20484)! | 11 |
| Microsoft 365 Apps | 2511 (Build 16.0.19426.20260) | 11 |
| Microsoft Azure CLI | 2.82.0 | 2 |
| Microsoft Azure Kubelogin | 0.2.14 | 2 |
| Microsoft Edge Beta | 144.0.3719.82 | 11 |
| Microsoft Edge for Business | 144.0.3719.82 | 11 |
| Microsoft Edge for Business | 144.0.3719.104 | 1 |
| Microsoft Edge for Business | 144.0.3719.92 | 1 |
| Microsoft Edge for Business | 143.0.3650.139 | 1 |
| Mozilla Firefox | 147.0.2 | 2 |
| Mozilla Firefox | 147.0 | 16 |
| Mozilla Firefox ESR 115 | 115.32.0 | 5 |
| Mozilla Firefox ESR 140 | 140.7.0 | 13 |
| Mozilla Thunderbird | 147.0 | 16 |
| Mozilla Thunderbird | 147.0.1 | 1 |
| Mozilla Thunderbird ESR 140 | 140.7.0 | 13 |
| Mozilla Thunderbird ESR 140 | 140.7.1 | 1 |
| Mozilla Thunderbird ESR 140 | 140.7.1 | 2 |
| Node.js 20 LTS | 20.20.0 | 6 |
| Node.js 22 LTS | 22.22.0 | 6 |
| Node.js 24 | 24.13.0 | 6 |
| Node.js 25 | 25.3.0 | 7 |
| OpenSSL | 3.5.5 | 12 |
| OpenSSL | 3.3.6 | 10 |
| OpenSSL | 3.6.1 | 12 |
| OpenSSL | 3.4.4 | 11 |
| OpenSSL | 3.0.19 | 8 |
| OpenSSL Light | 3.5.5 | 12 |
| OpenSSL Light | 3.6.1 | 12 |
| OpenSSL Light | 3.4.4 | 11 |
| OpenSSL Light | 3.0.19 | 8 |
| OpenSSL Light | 3.3.6 | 10 |
| Oracle Java Runtime Environment Version 8 | 8.0.4810.10 | 4 |
| Oracle Java SE Development Kit | 25.0.2.0 | 4 |
| Oracle Java SE Development Kit 21 | 21.0.10.0 | 4 |
| Oracle Java SE Development Kit 8 | 8.0.4810.10 | 4 |
| Pale Moon | 34.0.0 | 6 |
| TeamCity | 2025.11.2 | 1 |
| Vivaldi | 7.7.3851.67 | 1 |
| Waterfox | 6.6.8 | 13 |
| Wireshark | 4.4.13 | 2 |
| Zulu JDK 11 (LTS) | 11.86.19 | 3 |
| Zulu JDK 17 (LTS) | 17.64.15 | 3 |
| Zulu JDK 21 (LTS) | 21.48.15 | 3 |
| Zulu JDK 25 (LTS) | 25.32.17.0 | 3 |
| Zulu JDK 8 (LTS) | 8.92.0.19 | 3 |
| Zulu JRE 11 (LTS) | 11.86.19 | 3 |
| Zulu JRE 17 (LTS) | 17.64.15 | 3 |
| Zulu JRE 21 (LTS) | 21.48.15 | 3 |
| Zulu JRE 25 (LTS) | 25.32.17.0 | 3 |
| Zulu JRE 8 (LTS) | 8.92.0.19 | 3 |
Application management at the speed of your operations
Vulnerabilities move fast, especially in a distributed workforce. Discover how Recast’s application management product, Application Workspace, helps IT teams keep applications patched, compliant, and correctly configured, wherever work happens.



