Introduction
Microsoft has tightened security requirements around certificate-based authentication. As of September 9, 2025, Active Directory enforces strong mapping for certificate logons, closing the door on weaker mapping methods that left organizations exposed.
For endpoint admins, this means the change is already in effect. If your certificates were not updated in time, authentication failures may already be occurring. Now is the time to review templates, policies, and Intune profiles to get back in compliance.

What is Strong Mapping?
In Active Directory, certificate mapping is used to bind a certificate to a user or device account. Traditionally, many organizations have relied on weak mapping methods such as UPN or email address matching. The problem: these identifiers can be spoofed or mismatched, creating opportunities for abuse.
Strong mapping instead uses the certificate’s ObjectSID, tightly coupling the certificate to the AD account.
- Weak mapping = flexible but insecure
- Strong mapping = strict, cryptographically enforced, resistant to spoofing

Who Has Been Affected Since September 9?
Certificate-based authentication against Active Directory is where problems arise. If certificates were issued without including the SID, authentication now fails. Organizations that did not prepare before the deadline may already be experiencing logon or connectivity issues.
✅ Impacted scenarios:
- Smart card logon to Windows devices via AD (user certificates)
- VPNs or Wi-Fi that use AD certificate authentication (user certificates)
- Device authentication workflows tied to AD (device certificates)
❌ Not impacted:
- Cloud-only authentication (Azure AD / Entra ID)
- SaaS apps using SAML or OIDC
- Wi-Fi or VPN solutions that do not use AD

Why This Matters for Endpoint Security
Weak mapping has been a known attack vector for years. Attackers could create a certificate with a spoofed UPN, present it to AD, and gain access without owning the legitimate account. Strong mapping closes this gap.
For endpoint admins, this is a security hardening step that helps enforce Zero Trust principles: identity should be tied to verifiable cryptographic material, not a text field.

How to Prepare: Step-by-Step
1. Inventory Current Certificates
Run a discovery of certificates in use for logon.
- Device certificates (stored in the Local Machine store):
Get-ChildItem Cert:\LocalMachine\My
- User certificates (stored in the Current User store):
Get-ChildItem Cert:\CurrentUser\My
- Check Intune reports for devices with issued user or device certs
- Document which certificate templates are being used
2. Check Mapping Method
Review your AD Certificate Services (ADCS) templates.
- Identify if UPN/email mapping is used
- Flag templates that are not configured for strong mapping
3. Update Certificate Templates
Configure templates to require strong mapping.
- In ADCS, set the mapping to include the SID (ObjectSID)
- Update issuance policies to match
4. Pilot in Intune
Push updated certificate profiles to a test group.
- Use Intune to deploy updated SCEP certificate profiles for both users and devices
- Carefully review the Subject Name and SAN settings. Incorrect formats (such as short names instead of UPN) can cause authentication failures now that Strong Mapping is enforced
- Verify logon to AD-joined or hybrid devices
- Monitor event logs for mapping failures
- If you remove an assigned SCEP profile in Intune, the corresponding certificate is automatically revoked on the device. You can then create a new profile and deploy it to reissue certificates
Before (legacy SCEP profile without SID):
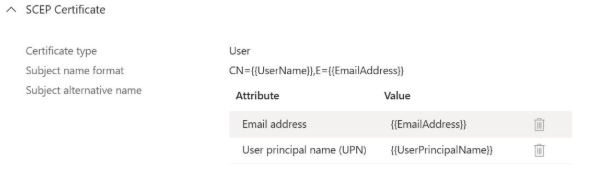
After (updated SCEP profile with SID):
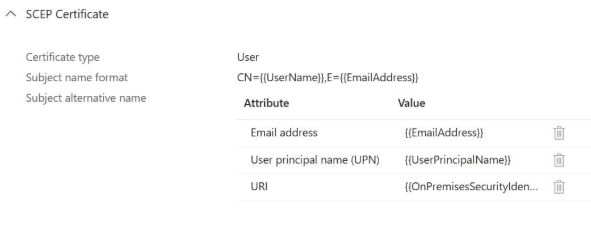
When configuring the SAN settings, use the following value for the SID:
Attribute type: URI
Value: {{OnPremisesSecurityIdentifier}}
This will result in certificates being issued with a SAN entry like:
tag:microsoft.com,2022-09-14:sid:<objectSID>

How to Verify if SID Is Included
On a client device, you can open the issued certificate and check the Subject Alternative Name (SAN) field. If Strong Mapping is correctly applied, you will see the ObjectSID value listed.
If the SID is missing, the certificate will not authenticate against Active Directory after the enforcement date.

5. Scale & Communicate
Once pilot success is confirmed:
- Roll out policies to all hybrid/AD-joined devices
- Communicate to helpdesk: failed logons may be caused by expired or weakly mapped certs
- Provide users with re-enrollment instructions if needed

Common Pitfalls to Avoid
- Skipping inventory: If you don’t know what certs are in play, you’ll miss critical scenarios
- No pilot: Rolling out strong mapping to all devices without testing is a recipe for lockouts
- Ignoring hybrid edge cases: Even if you’re “mostly Intune,” hybrid users logging on with AD may still break

Conclusion
The September 9, 2025, enforcement of strong mapping is a hard stop, not just a recommendation. If your environment still relies on weakly mapped user or device certificates, outages and authentication failures are inevitable. By reviewing templates, updating SCEP profiles, and ensuring SID inclusion for both users and devices, you can close a long-standing security gap and keep authentication workflows running smoothly.


