Systems Management
How to Configure Windows LAPS in Active Directory
Topics: Systems Management
This guide to setting up LAPS in Active Directory is the first part of a two-part series about configuring Windows LAPS. This post covers setting up LAPS with on-premises Active Directory. The next guide will cover setting up LAPS with Entra ID (Azure Active Directory).
It’s important to note that the features of Windows LAPS vary if you are using the Active Directory version or the Entra ID (Azure Active Directory) version. More information about features and architecture can be found here.
Table of Contents
- Prerequisites and Notes
- Setting Up Windows LAPS
- Configuring Group Policy
- Group Policy Descriptions
- Verifying success
Prerequisites and Notes
Before configuring Windows LAPS in Active Directory, there are a couple of important prerequisites and notes about what is required for functionality.
- The first involves Domain Functional Level (DFL).
- Full Windows LAPS features, encryption of passwords, and Directory Services Restore Mode (DSRM) password encryption, only works with a DFL of 2016. If you are below a DFL of 2016, you cannot encrypt LAPS passwords in AD, or use LAPS to encrypt your DSRM.
- If you are on a Domain Functional Level of 2016, and have Windows Server 2016 Domain Controllers, you can encrypt the passwords, but you cannot use LAPS to manage your DSRM.
- If you are on a Domain Functional Level of 2016 and have Windows Server 2019 or 2022 Domain Controllers, you can use all the features of Windows LAPS.
- The versions of Windows and Windows Server required to use Windows LAPS:
- Windows 11 Professional, Education, or Enterprise
- Windows 10 Professional, Education, or Enterprise
- Windows Server 2022 and Windows Server Core 2022
- Windows Server 2019
Setting Up Windows LAPS: Step by Step
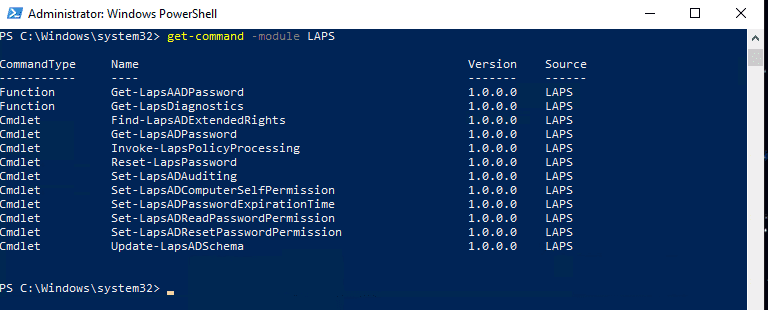
1. Check for the PowerShell Module
The PowerShell module should be available on Windows 2019 and 2022 that have been updated to at least the April 2023 Cumulative Update. However, you can confirm that the PowerShell module for LAPS has been added by using the command Get-Command –Module LAPS. You should see the below response if the PowerShell module has been added.
2. Extend the Active Directory Schema
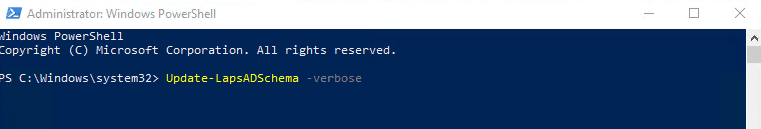
In order for Windows LAPS to work you will need to extend the Schema with the new attributes that are required. Make sure you are a schema admin and enter the following command:
Update-LapsADSchema –verbose The command will ask you if you want to extend the AD Schema, type “A” to add all the schema extensions that are needed. The –verbose parameter in the command will show additional information about what the command is doing and can be omitted if desired.
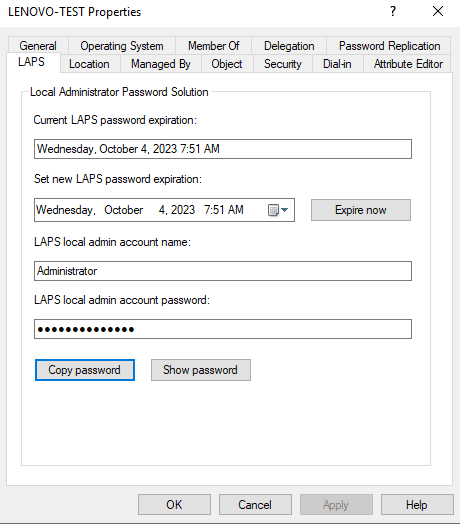
3. Verify the Schema was Extended
You can verify the schema was extended by looking at the computer object in Active Directory Users and Computers. You should see a new LAPS tab. It will not be populated with data until you set up the policies in Group Policy.
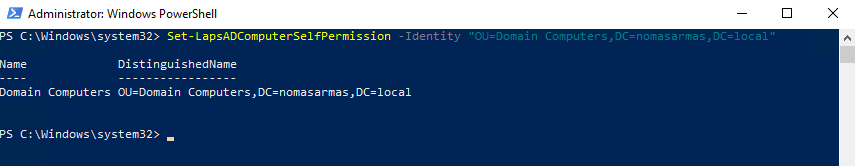
4. Set the AD LAPS Computer Permission
Next we need to set the OU (or multiple OU’s) in which the computers will have permission to change their password. The command is
set-lapsadcomputerselfpermission –identity “<Name of OU>”
You may need to use the full distinguishedname for the command to work as in the command below.
5. Configuring Group Policy
There are two group policy settings that must be set for LAPS to function, others are optional and can be applied as needed.
- Open group policy editor
- Create new Computer Policy
- Edit the policy and navigate to “Computer Configuration -> Policies -> Administrative Templates -> System -> LAPS”
Group Policy Descriptions
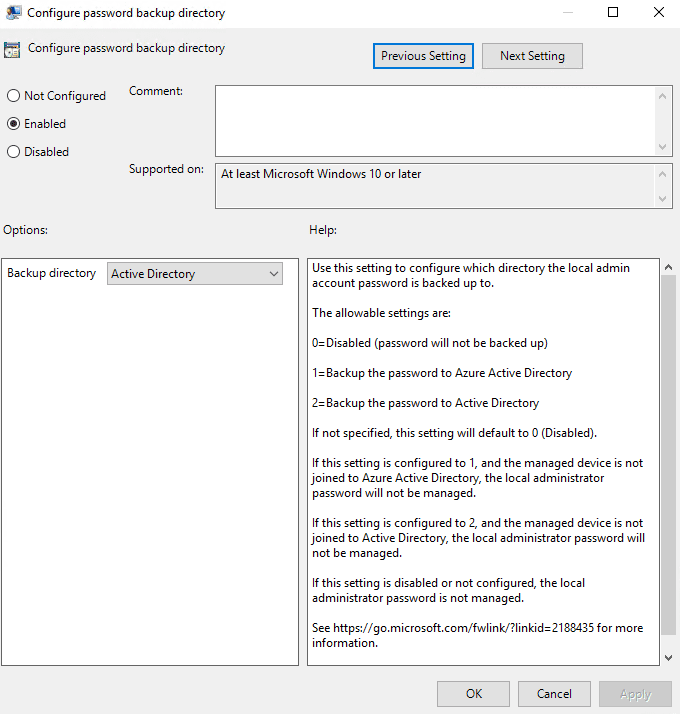
6. Configure Password Backup Directory (required)
With this group policy setting you determine if the password is going to be stored in Active Directory, or Azure Active Directory (Entra ID).
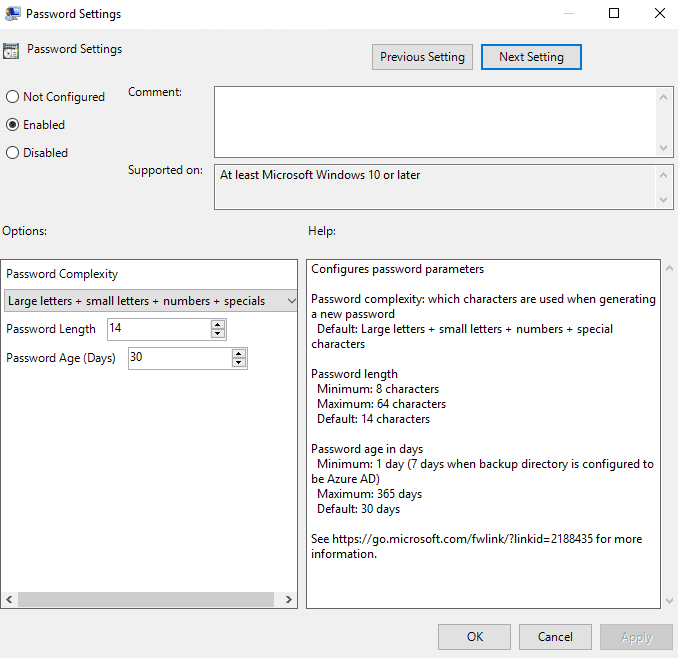
7. Password Settings (required)
This policy setting determines the password complexity, password length, and password age in days.
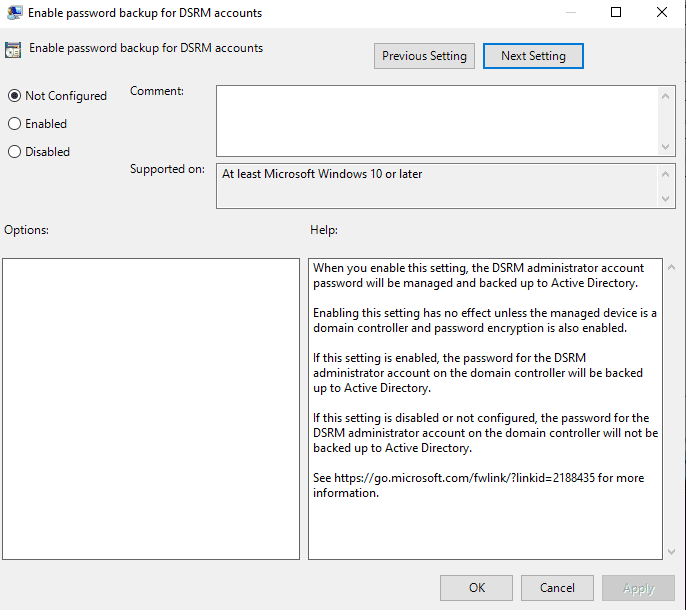
8. Enable Password Backup for DSRM Accounts (optional)
This setting allows the DSRM Administrator account to be backed up to Active Directory. Password encryption must be enabled for this setting to apply.
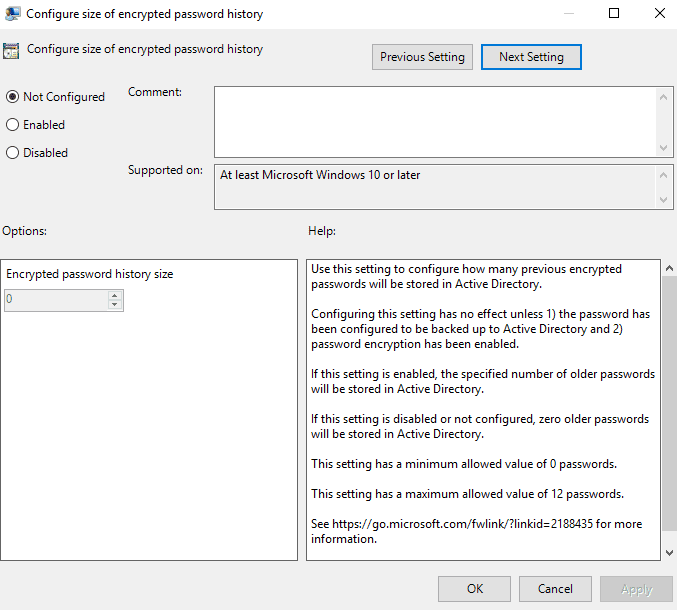
9. Configure Size of Encrypted Password History (optional)
This setting configures how many pervious encrypted passwords will be saved in Active Directory. The minimum that are stored is 0, the maximum is 12.
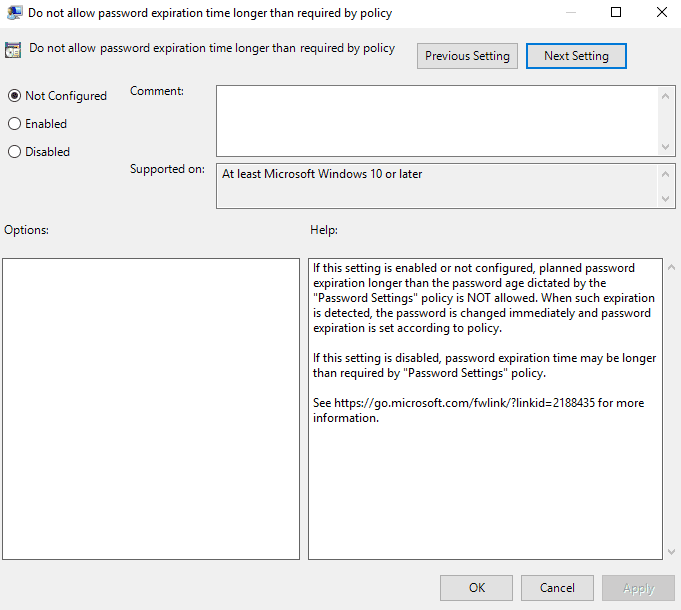
10. Enable Password Encryption (optional)
This setting determines if passwords will be encrypted when they are stored in Active Directory.
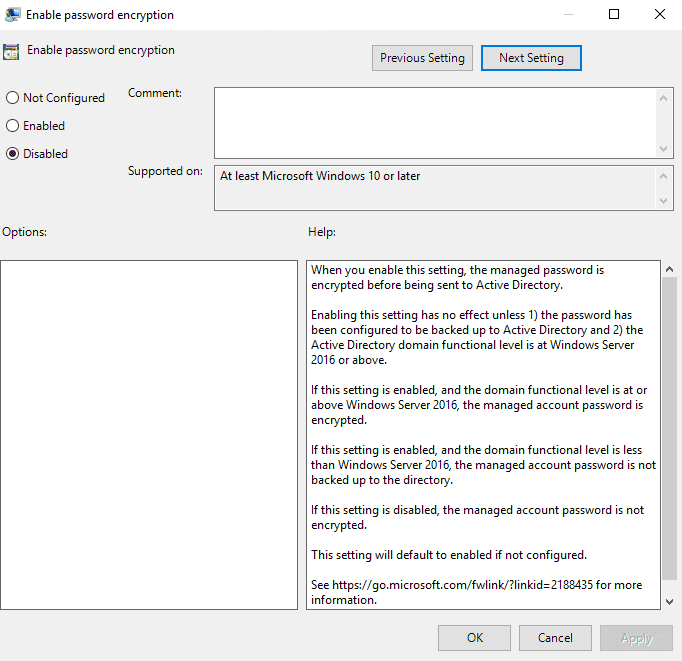
11. Configure Authorized Password Descriptors (optional)
This setting determines the specific user or group who is authorized to decrypt encrypted passwords.
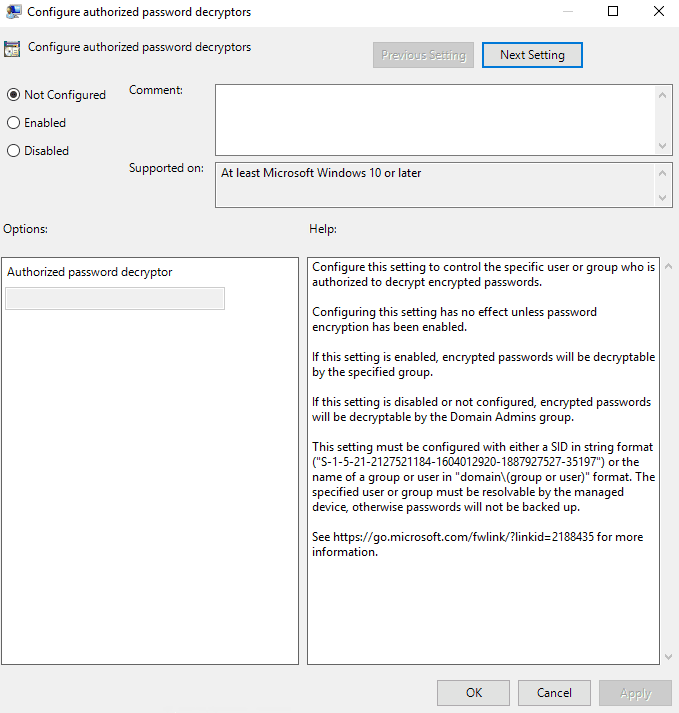
12. Name of Administrator Account to Manage (optional)
This setting specifies a custom Administrator account for which to manage the password if you are using an account that is not the built in Administrator account.
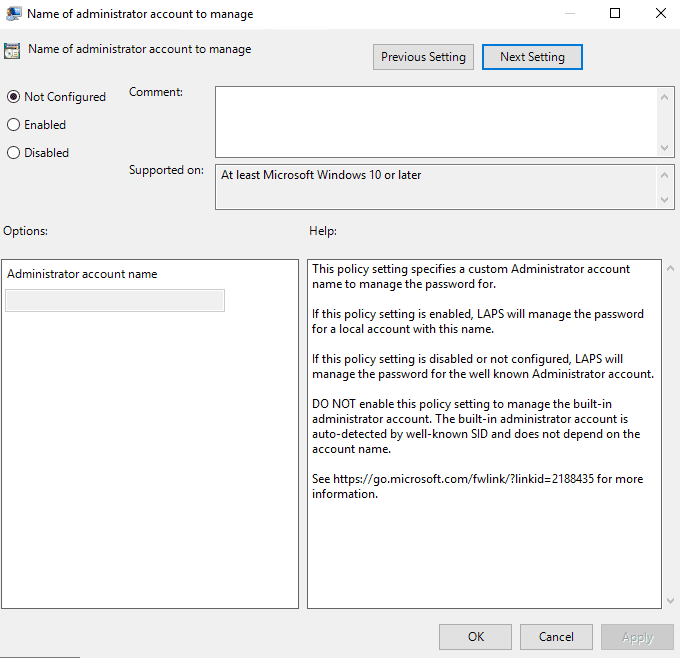
13. Do not Allow Password Expiration Time Longer than Required by Policy (optional)
With this setting, passwords are not allowed to have expiration times that are beyond the age dictated by the “password settings” policy.
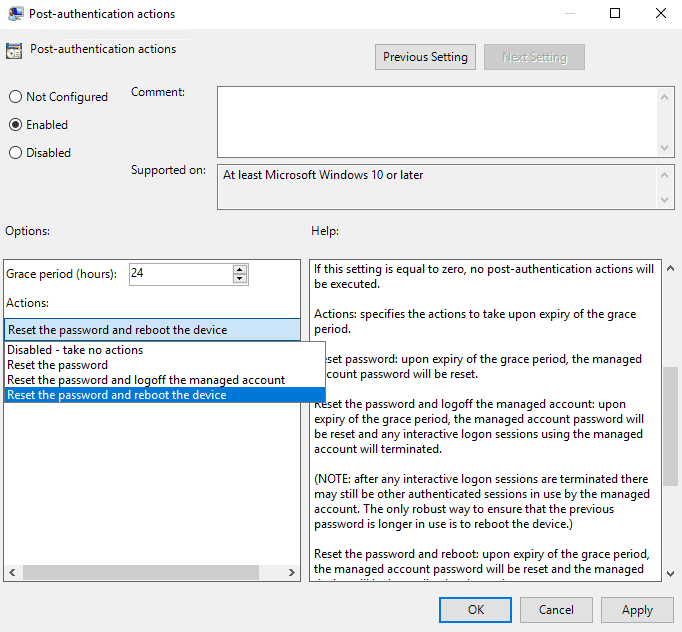
14. Post-authentication Actions (optional)
This setting determines the actions to take after the administrator password has been used, and the grace period before the action is taken in hours.
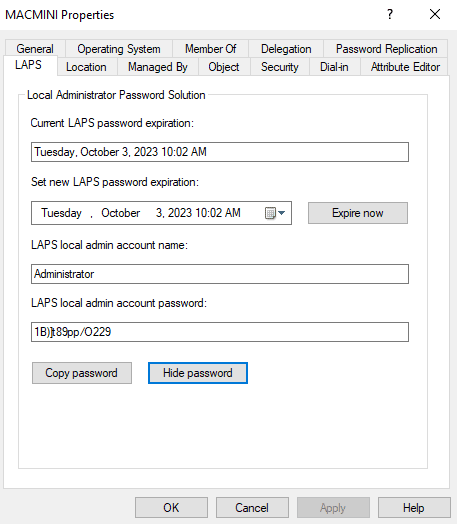
15. Verifying Success and Retrieving Passwords
After you have configured the group policies, you should run gpupdate /force and allow group policy to update. If everything is working correctly you will see password information in your Active Directory Users and Computer Object. Select “Copy Password” to copy the administrator password to your clipboard.
A Wrap: How to Configure Windows LAPS in Active Directory
I hope this guide helped you with your Windows LAPS configuration. Watch for our next guide covering how to set up LAPS with Entra ID (formerly Azure AD).


































