Intune
How to Configure BitLocker with Intune: Device Configuration Profile Method
Topics: Intune
This post covers how to configure BitLocker with Intune using the Device Configuration Profile Method.
Microsoft allows for two different methods of creating BitLocker policies in Intune, and specifically states that both will get the same results (an encrypted computer) when you are completed.
Table of Contents
- Notes
- Prerequisites
- Intune Settings
- Verify the policy applied correctly
Note
This post and the accompanying screenshots were taken just after Microsoft rebranded Azure Active Directory to Entra ID. Most of the screenshots still show Azure Active Directory, but this name can be substituted with Entra ID interchangeably, as it was simply a marketing change and does not affect functionality in any way.
Prerequisites for Configuring BitLocker in Intune
Before you can configure BitLocker with Intune, you need to verify that you have the correct licenses in place in Entra ID and Intune. Additionally, the endpoint devices themselves have the following requirements:
- Intune License and Intune permissions to manage BitLocker
- Device must be Entra ID (Azure Active Directory) joined
- Devices must not be encrypted with a third-party encryption tool
- Devices must have a functional TPM
- Devices must have UEFI enabled on the drive
Intune Settings
How to configure BitLocker using the Device Configuration Profile:
1. Sign into the Intune Admin Center
2. Select Devices -> Configuration profiles -> Create profile
3. Select
- Platform: Windows 10 and Later
- Profile Type: Templates
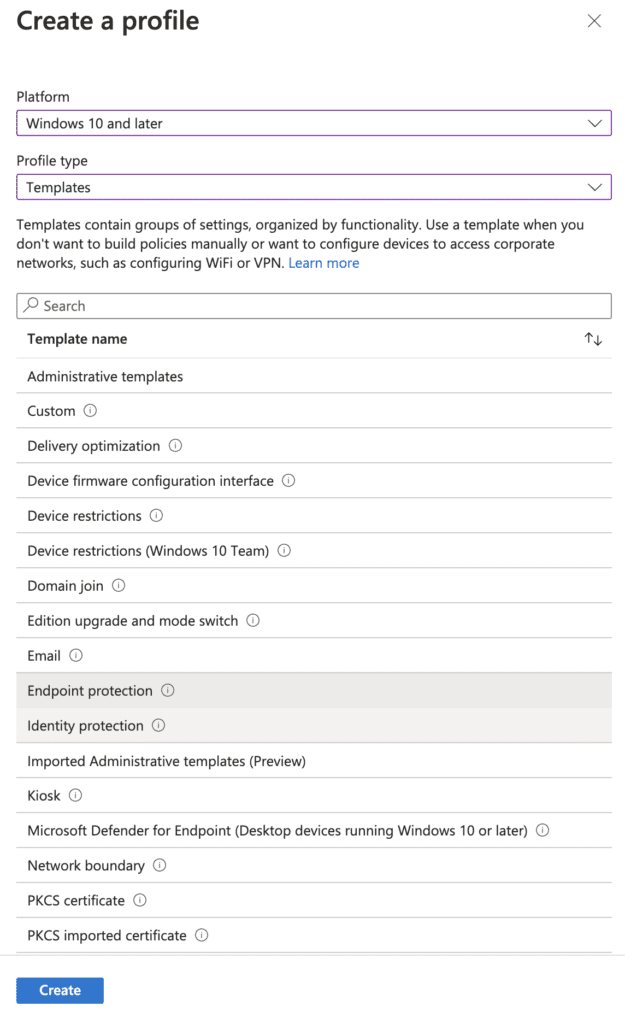
4. Click “Endpoint Protection”
5. Click “Create”
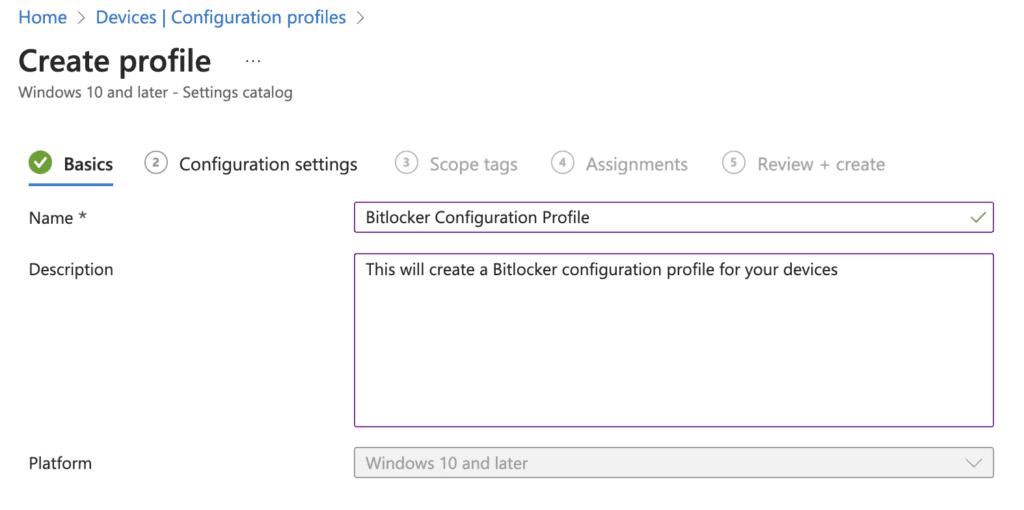
6. Enter a Name and Description for your Configuration Profile. Click Next.
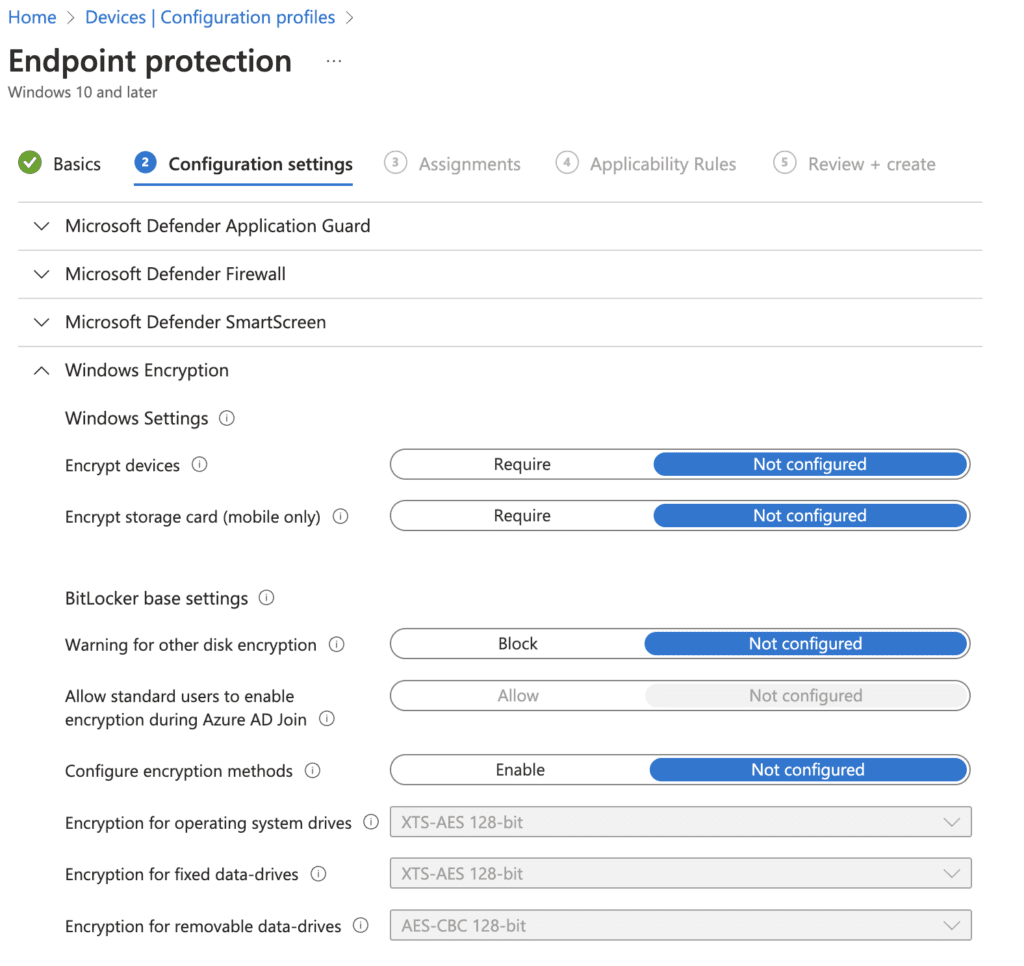
7. Expand Windows Encryption
Set BitLocker settings as desired
- Windows Settings – will apply to all versions of Windows 10 and later
- Encrypt Devices – Setting to require will enable BitLocker device encryption
- Encrypt storage card (mobile only) – Require will encrypt the storage card of a mobile device
- BitLocker Base settings – Settings are universal BitLocker settings for all types of data drives
- Warning for other disk encryption – Prompts if any third-party disk encryption is being used. Blocking will disable this warning.
- Allow standard users to enable encryption during Azure AD join – Allows non-admin users to enable BitLocker at the time the devices are joined to Azure AD.
- Configure encryption methods – Allows you to configure the encryption methods for OS drives, Fixed Data Drives, and Removable Data Drives
- Encryption for Operating System drives – XTS-AES Algorithm is recommended. Changing the encryption method has no effect if the drive is already encrypted or if encryption is in progress.
- Encryption for fixed data-drives – XTS-AES Algorithm is recommended. Changing the encryption method has no effect if the drive is already encrypted or if encryption is in progress.
- Encryption for removable data-drives – ATS-CBC Algorithm is recommended if the removable drive will be used with other devices that are not running Windows 10 or 11
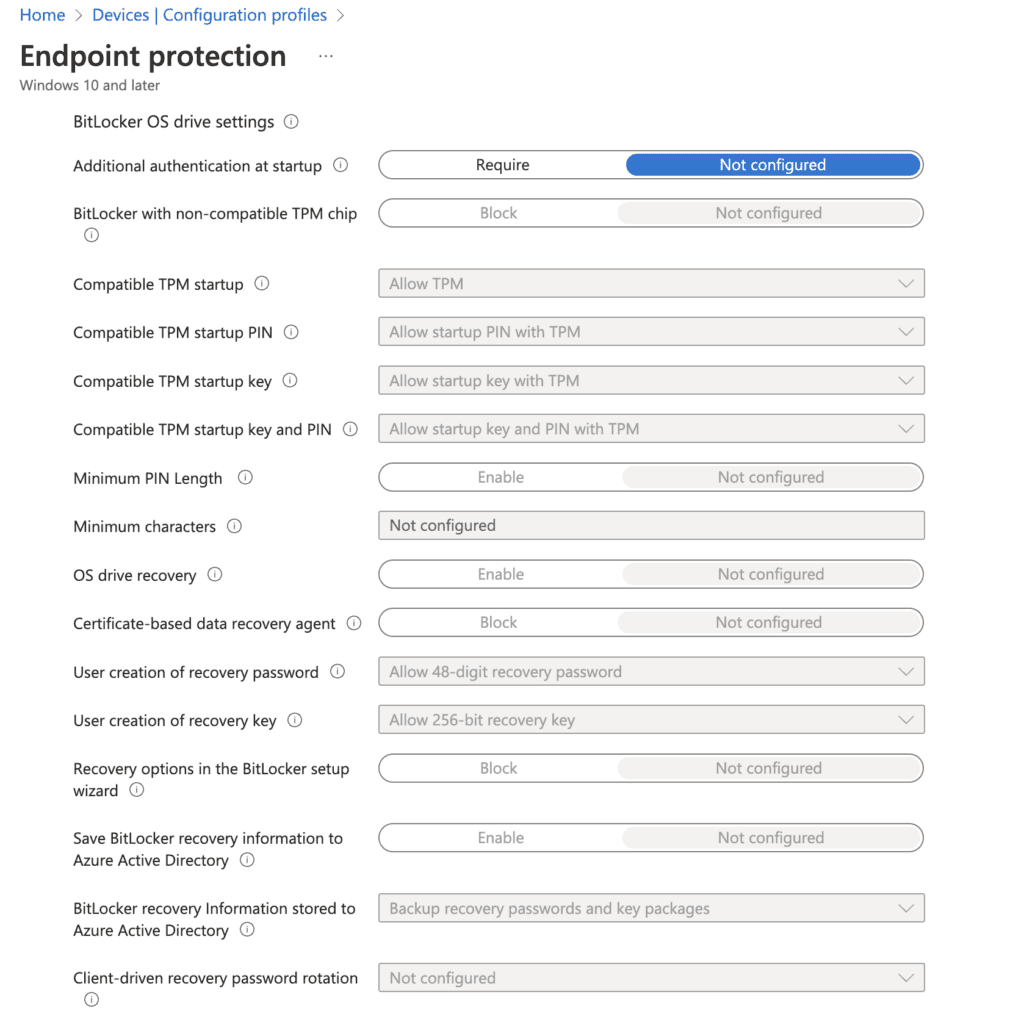
- BitLocker OS Drive Settings – These settings apply specifically to operating system data drives
- Additional authentication at startup – “Require” allows you to configure the additional authentication requirements at system startup, including the use of a TPM or Startup PIN
- BitLocker with non-compatible TPM chip – Block the use of BitLocker on a computer without a compatible TPM chip
- Compatible TPM startup – Configure if TPM is allowed, required, or not allowed
- Compatible TPM startup PIN – Configure if a TPM startup PIN is allowed, required, or not allowed
- Compatible TPM startup key – Configure if a TPM startup key is allowed, required, or not allowed
- Compatible TPM startup key and PIN – Configure if a TPM startup key and PIN is allowed, required, or not allowed
- Minimum PIN length – Selecting “Enable” will allow you to set the minimum startup PIN length. If this setting is not configured and a TPM PIN is required, the default value will be 6 characters.
- Minimum Characters – Startup PINs can range from 4-20 digits in length
- OS Drive recovery – Control how BitLocker protected OS drives are recovered in the absence of required startup key information
- Certificate-based data recovery agent – Block the use of data recovery agent with BitLocker protected OS drives Policy Editor
- User creation of recovery password – Configure if users are allowed, required, or not allowed to generate a 48-digit recovery password
- User creation of recovery key – Configure if users are allowed, required, or not allowed to generate a 256-bit recovery key
- Recovery options in the BitLocker setup wizard – Block users from specifying recovery options when they turn on BitLocker
- Save BitLocker recovery information to Entra ID (Azure Active Directory) – Enable BitLocker recovery information to be stored in Entra ID (Azure Active Directory)
- BitLocker recovery information stored to Entra ID (Azure Active Directory) – Configure what pieces of BitLocker recovery information are stored in Entra ID (Azure Active Directory)
- Client driven recovery password rotation – This setting initiates a client-driven recovery password rotation after an OS Drive Recovery
- Store recovery information in Entra ID (Azure Active Directory) before enabling BitLocker – Prevent users from enabling BitLocker unless the computer successfully backs up the BitLocker recovery information to Entra ID (Azure Active Directory).
- Pre-boot recovery message and URL – Enable the recovery and URL that are displayed on the pre-boot key recovery screen
- Pre-boot recovery message – Configure the option for the pre-boot recovery message Store recovery information in Entra ID (Azure Active Directory) before enabling BitLocker – Prevent users from enabling BitLocker unless the computer successfully backs up the BitLocker recovery information to Entra ID (Azure Active Directory).
- Pre-boot recovery message and URL – Enable the recovery and URL that are displayed on the pre-boot key recovery screen
- Pre-boot recovery message – Configure the option for the pre-boot recovery message
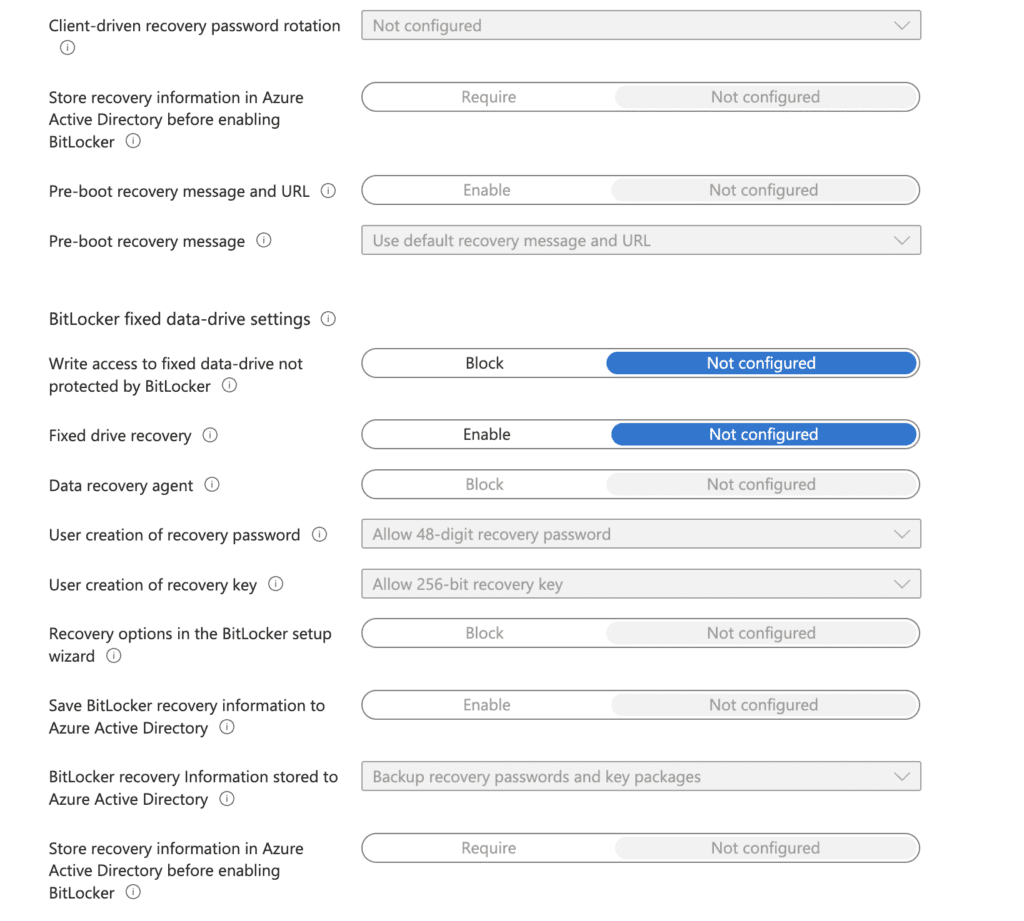
- BitLocker fixed data-drive settings – These settings apply specifically to fixed data drives
- Write access to fixed data-drive not protected by BitLocker – Selecting block will block data writes to any fixed drive that is not protected by BitLocker
- Fixed drive recovery – Control how BitLocker protected fixed data drives are recovered in the absence of the required startup key information
- Data recovery agent – Block the use of the Data Recovery Agent with BitLocker protected fixed drives Policy Editor
- User creation of recovery password – Configure if users are allowed, required, or not allowed to generate a 48-digit recovery password
- User creation of recovery key – Configure if users are allowed, required, or not allowed to generate a 256-bit recovery key
- Recovery options in the BitLocker setup wizard – Block users from specifying recovery options when they turn on BitLocker
- Save BitLocker recovery information to Entra ID (Azure Active Directory) – Enable BitLocker recovery information to be stored in Entra ID BitLocker Recovery information stored to Entra ID (Azure Active Directory) – Configure what pieces of BitLocker recovery information are stored in Entra ID
- Store recovery information in Entra ID (Azure Active Directory) before enabling BitLocker – Prevent users from enabling BitLocker unless the computer successfully backs up the BitLocker recovery information to Entra ID
- BitLocker removable data-drive settings – These settings apply to removable data drives
- Write access to removable data-drive not protected by BitLocker – Determine whether BitLocker protection is required for removable data-drives to be writable on a computer
- Write access to devices configured in another organization – Determine if removable data drives configured by an external organization can be written to

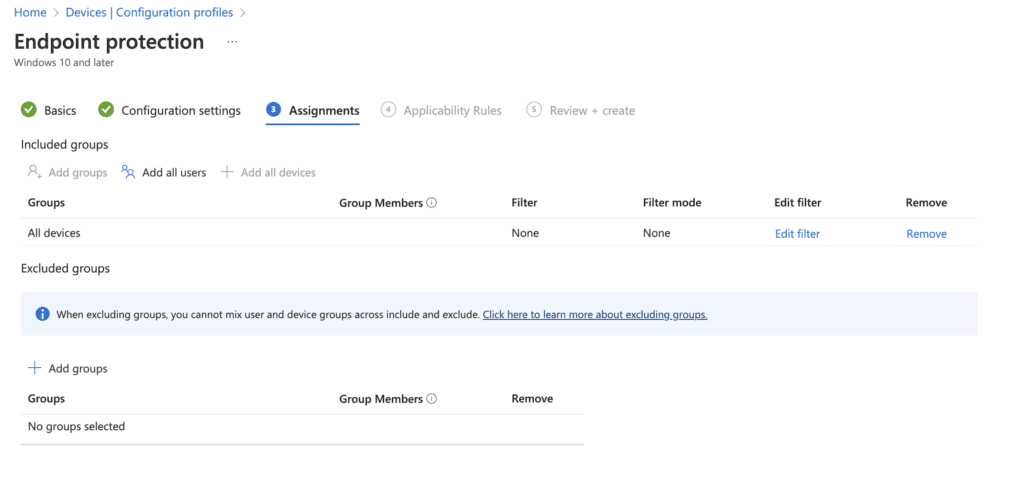
Select Assignments for the deployment
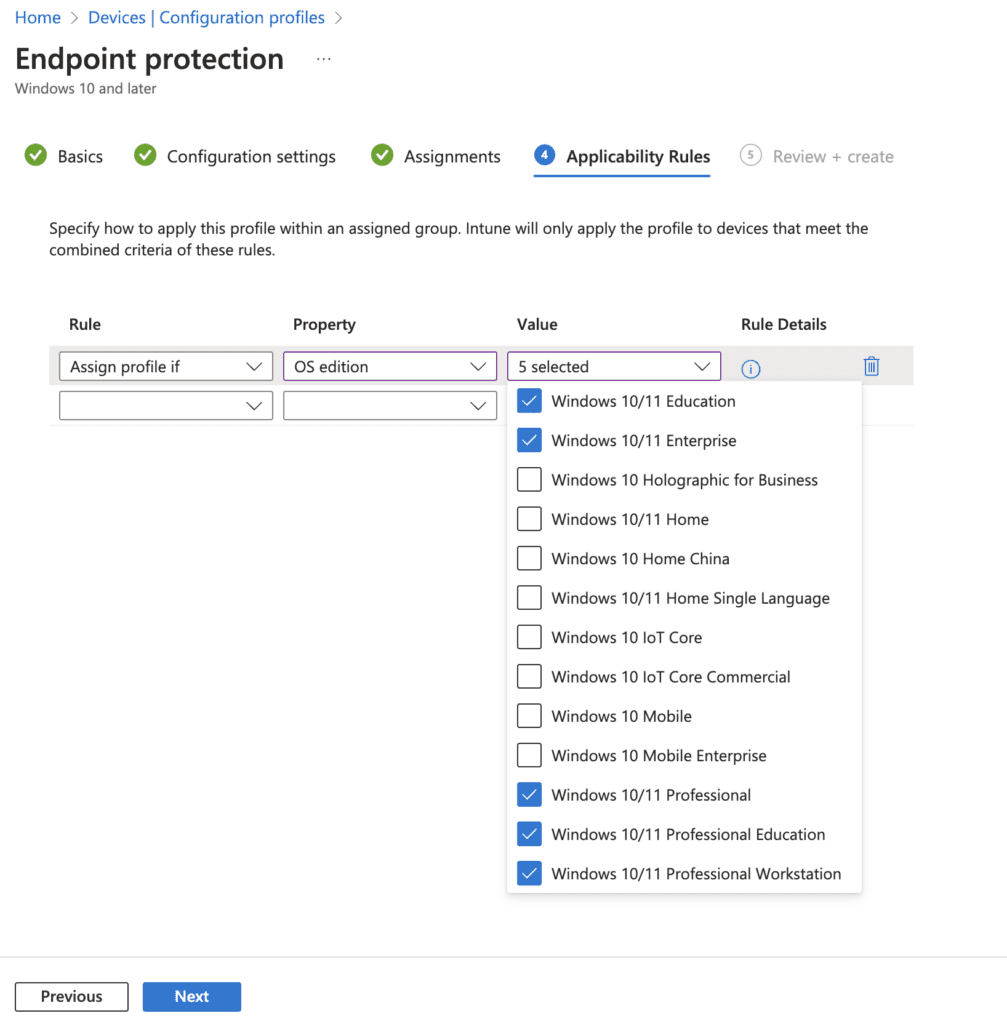
Select applicability rules for the deployment
Review and create the policy
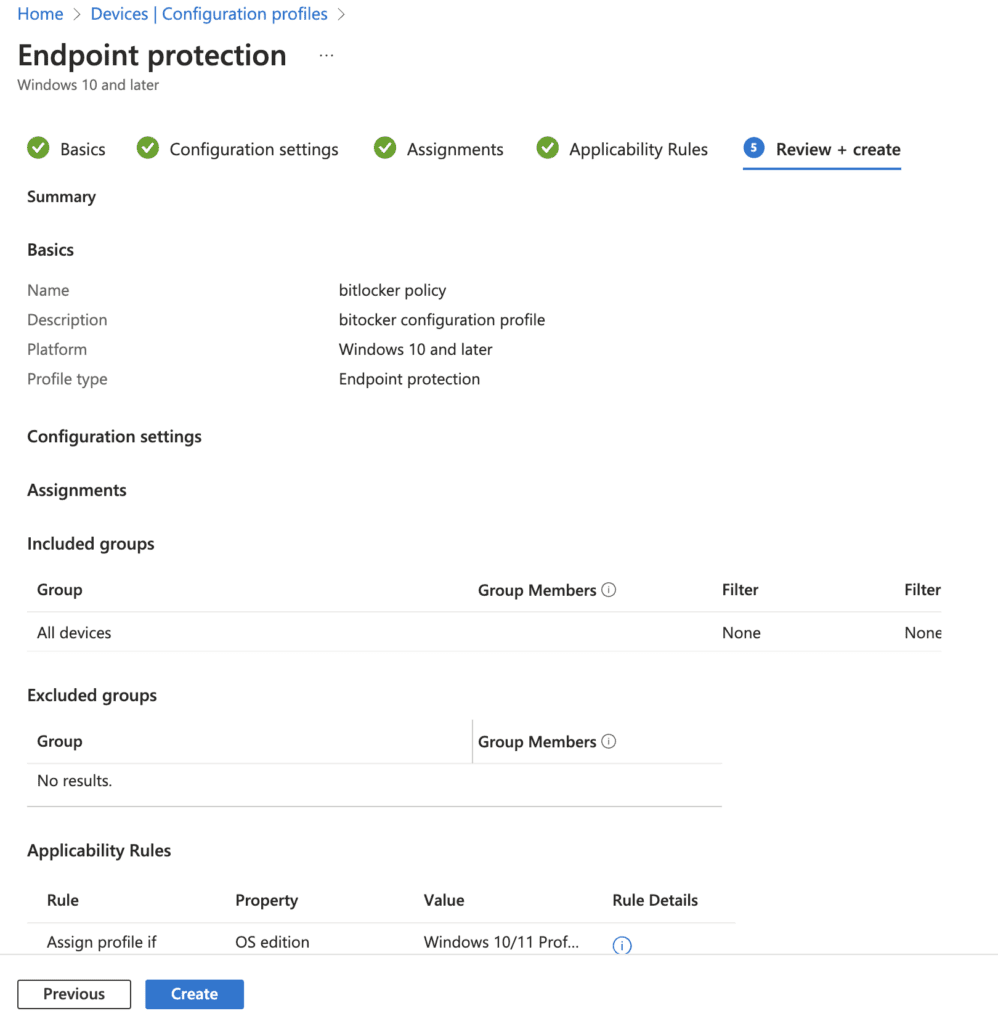
Verify the policy applied correctly
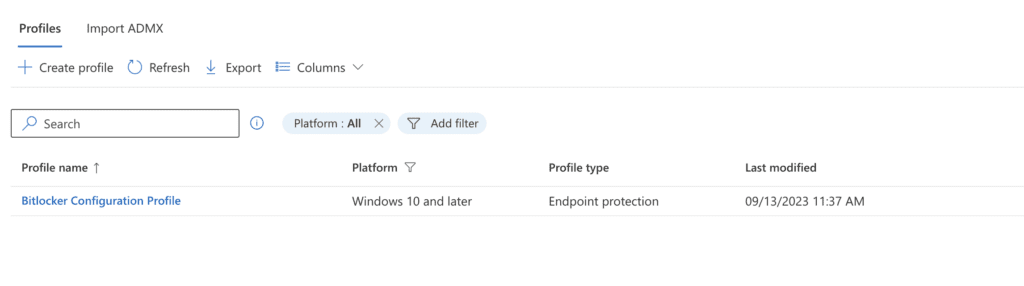
8. Policy will appear under “Configuration Profiles”
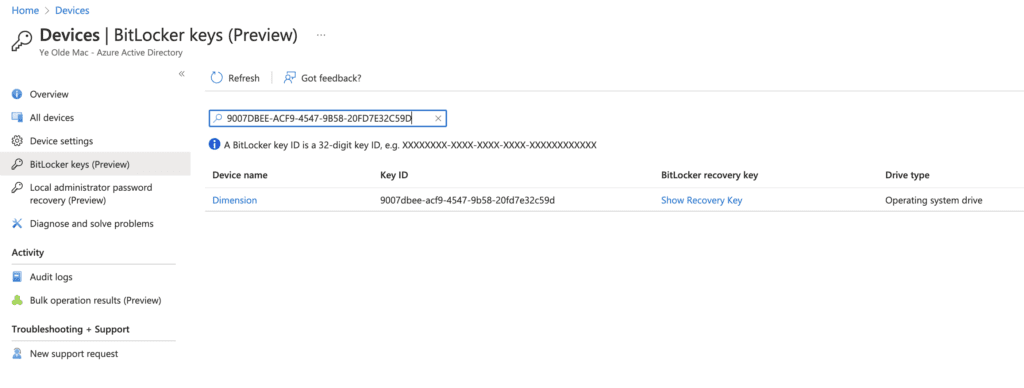
9. Check for the BitLocker Key in Entra ID under Devices -> BitLocker Keys
BitLocker is now Configured with Intune
Device Configuration Profile Method
You’ve successfully navigated this guide to configuring BitLocker through the Device Configuration Profile method in Intune. We’ve covered everything from prerequisites and settings to validation steps.
The keys to a strong BitLocker policy lie in accurate configuration, setting up proper recovery mechanisms, and ensuring that your endpoint devices meet the needed criteria. With this in place, you can best fortify your Windows environment, keeping both data and systems safeguarded.
Reach out via Twitter or email if you have any questions.