Intune
How to Set Up Mobile Application Management (MAM) for Windows with Intune
Topics: Intune
As an admin, have you ever dealt with an end user who lost or broke their laptop but still needed access to company resources? Did you wait a few days for a replacement laptop to arrive or did you allow them to access company data and resources on an unmanaged device, putting your organization at risk for data leaks? That is a tricky scenario, especially if your organization only allows managed devices to access company resources.
Luckily for admins, the Intune team has made Mobile Application Management (MAM) for Windows available since September 2023, allowing users to access company resources on unmanaged devices while still allowing IT teams to secure organizational data. While end users can only access organizational resources by going to Microsoft Edge on a Windows device and signing in with their org account (a limitation), this is still a solid option that allows administrators to protect data on personal, unmanaged Windows devices while giving access to end users without needing a company-owned device.
Understanding MAM with Intune: How It Works
Mobile Application Management (MAM) through Intune employs a robust strategy to safeguard organizational data as it’s accessed or shared across applications. This is achieved by:
- Applying App Protection Policies: These policies are pivotal in controlling how organizational data is accessed or shared within specified apps, ensuring that sensitive information remains secure regardless of the application in use.
- Verifying Device Integrity: Before any device is granted access to organizational data, its condition and health need to be assessed. This is done through the integration with the Windows Security Center, which evaluates the device’s security status to prevent compromised devices from accessing sensitive information.
- Enforcing Conditional Access with App Protection Policies: Access to organizational data on a Windows device should depend upon compliance checks with app protection policies. This conditional access ensures that only secure, policy-compliant devices can retrieve company data, which helps enhance security.
- Customizing User Experience with Application Configuration Policies: For a tailored application experience that meets both user needs and security requirements, administrators can deploy Application Configuration Policies. This allows for personalized and secure interactions with organizational apps.
With this grounding knowledge of how Intune’s MAM functions to protect and manage access to organizational data, let’s look at the prerequisites needed to implement this powerful tool.
Requirements
Devices:
- Windows 10, build 19045.3636, KB5031445 or later
- Windows 11, build 10.0.22621.2506, KB5031455 (22H2) or later
- Microsoft Edge (v117 stable branch and later for Windows 11 and v118.0.2088.71 and later for Windows 11)
Licenses:
- Microsoft Intune License
- Entra ID P1 License
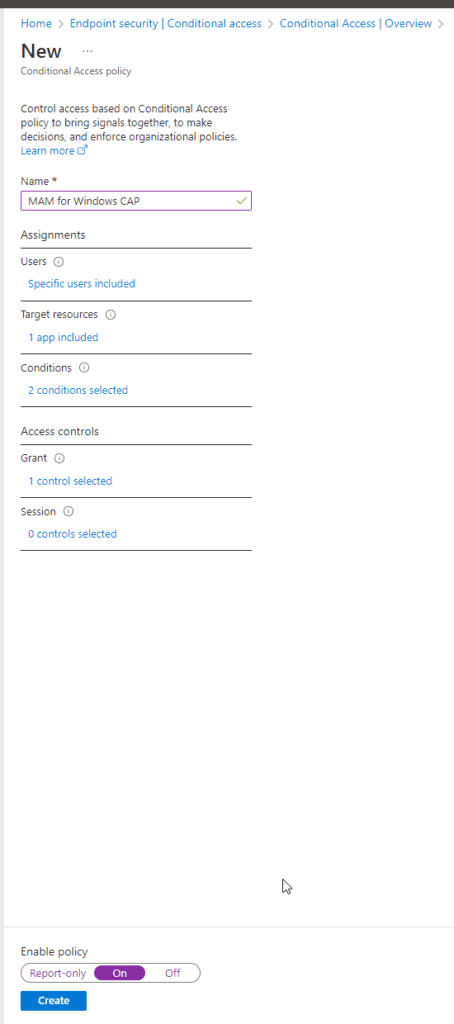
Step 1: Create a Conditional Access Policy
Head over to the Intune Admin Center and then the Endpoint Security section. Then under the Manage column select Conditional access.
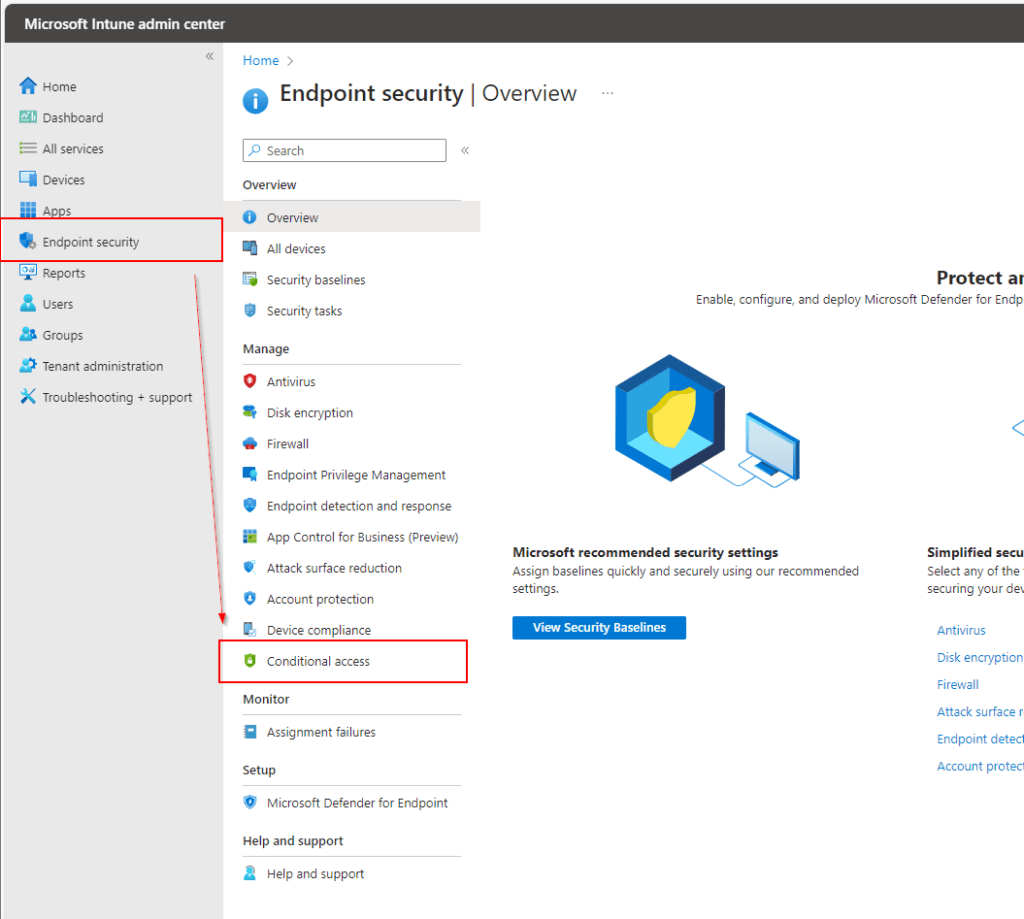
After clicking on Conditional access, you’ll land on the overview page and select + Create new policy.
Go ahead and pick your assignments — who must this Conditional Access policy apply to? In my case, I have a group that I named “App Protection Pilot Group.”
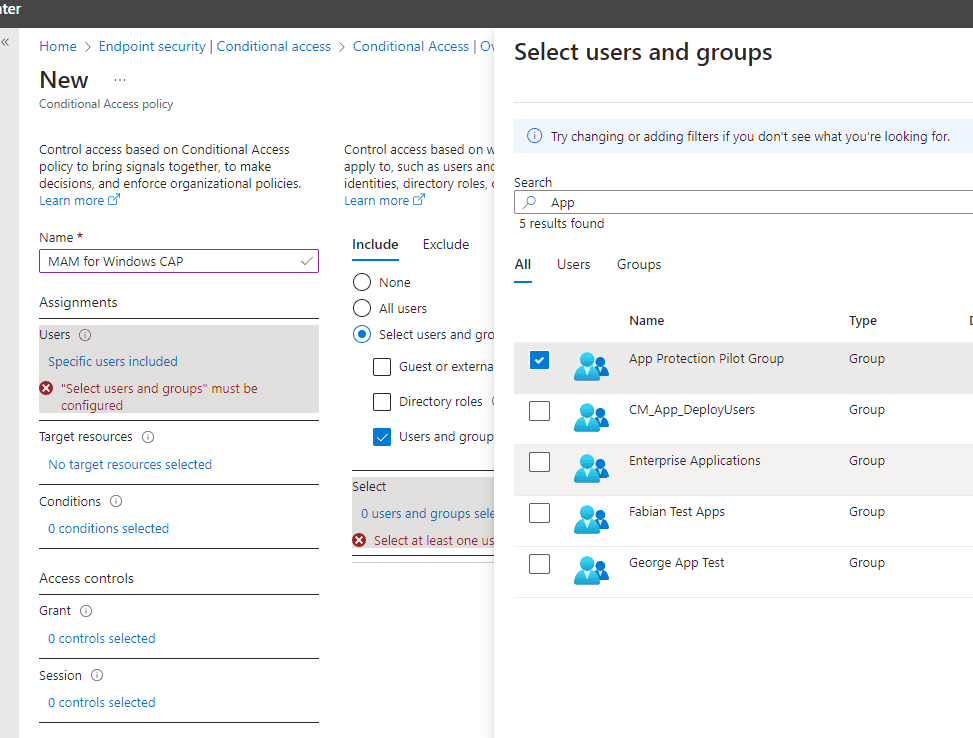
Now let’s target the resources we want to protect with MAM. I will go ahead and target Cloud Apps and select Office 365.
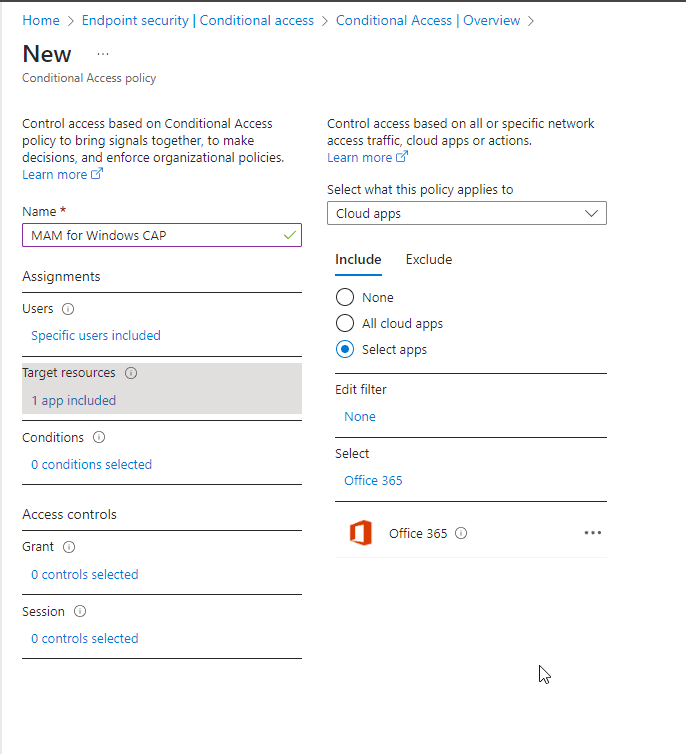
Now let’s set the condition to this policy. For windows MAM we’ll need to target the Windows Device platform, as this will tell us the platform the user is signing in from.
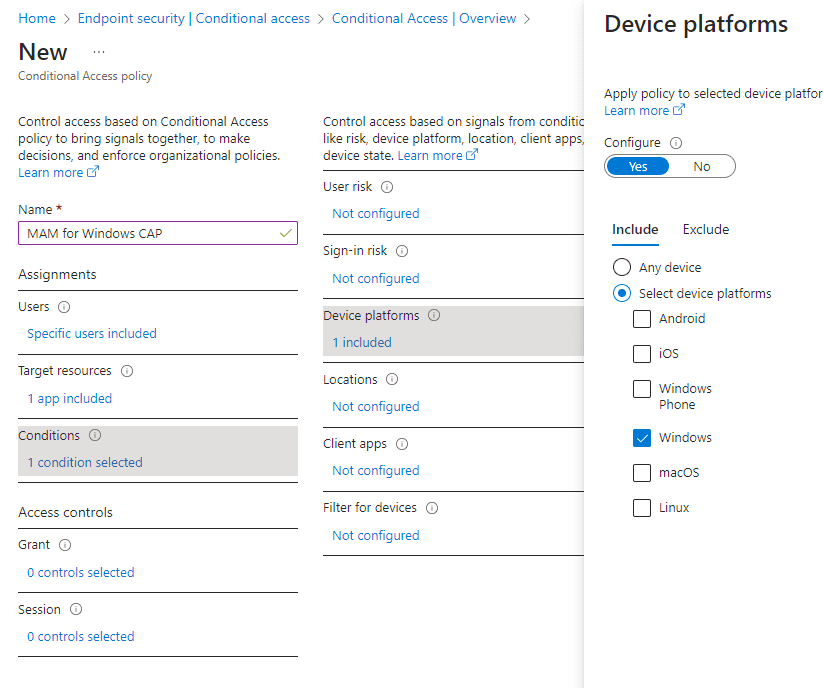
I have also set the client apps to Browser under the Conditions section.
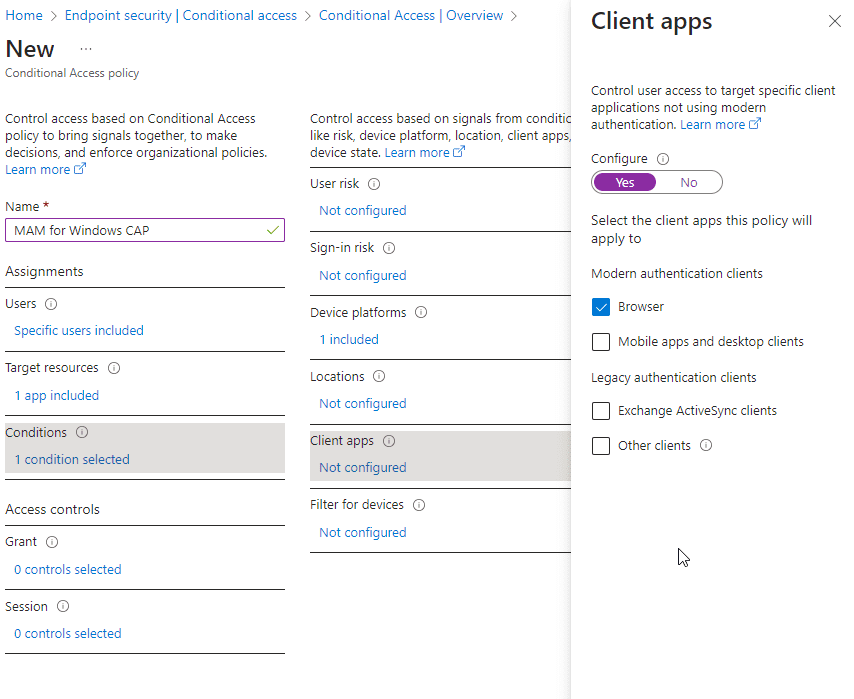
Lastly, we will enforce access by requiring an App Protection Policy.
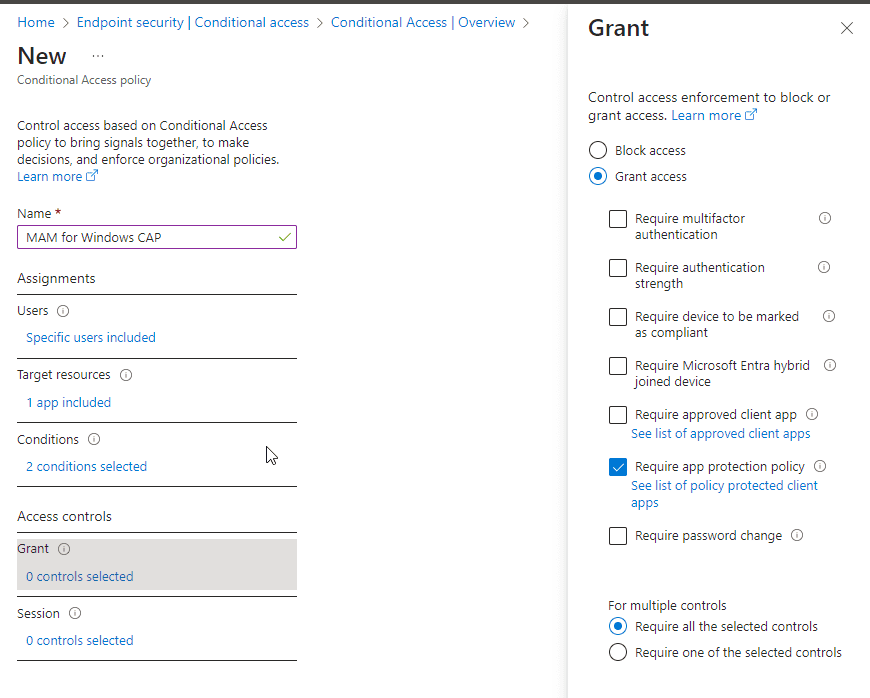
Now that the Conditional Access Policy is completed, enable the policy by moving the slider to On.
Step 2: Set up Windows Security Center
If we want to ensure the unmanaged devices accessing our company data are in a secure state, we can next set up the Windows Security Center. This will also be important later when creating the App Protection Policy.
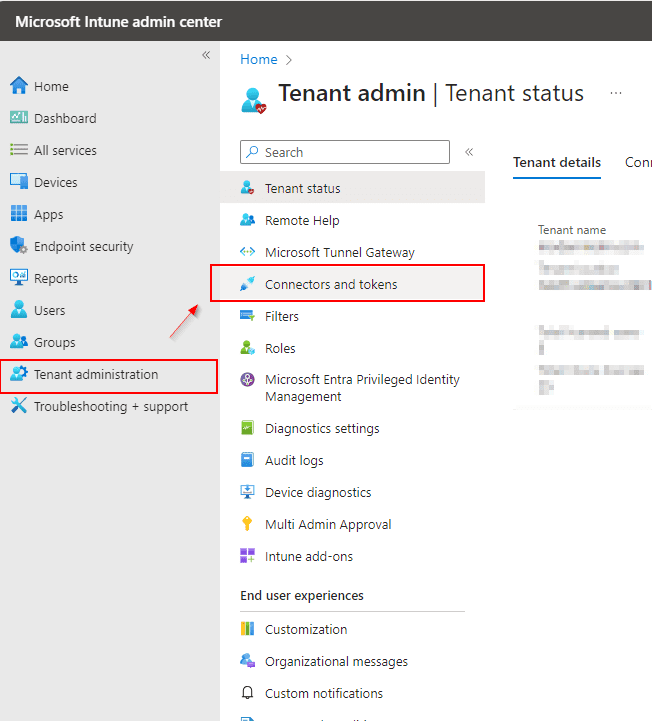
Go to Tenant administration in Microsoft Intune admin center > Connectors and tokens > Mobile Threat Defense.
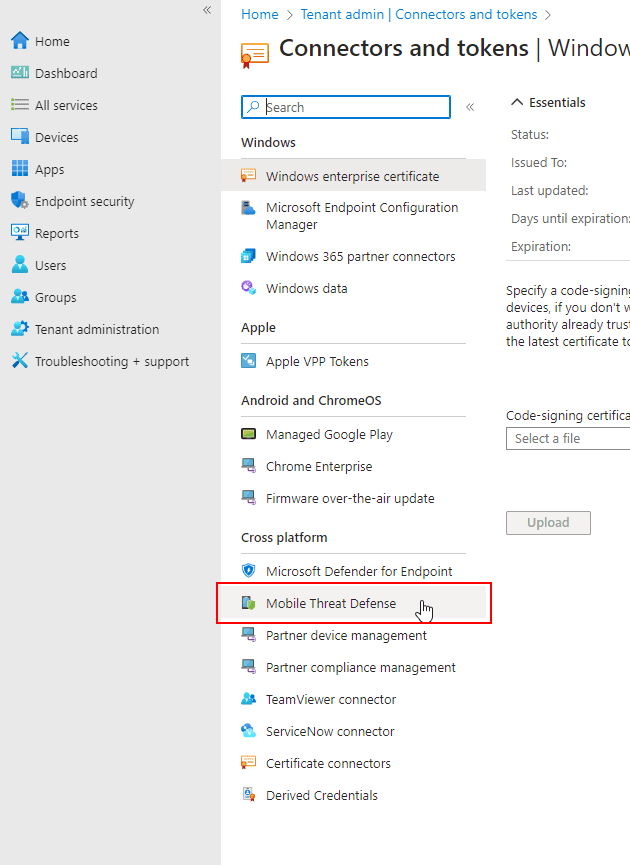
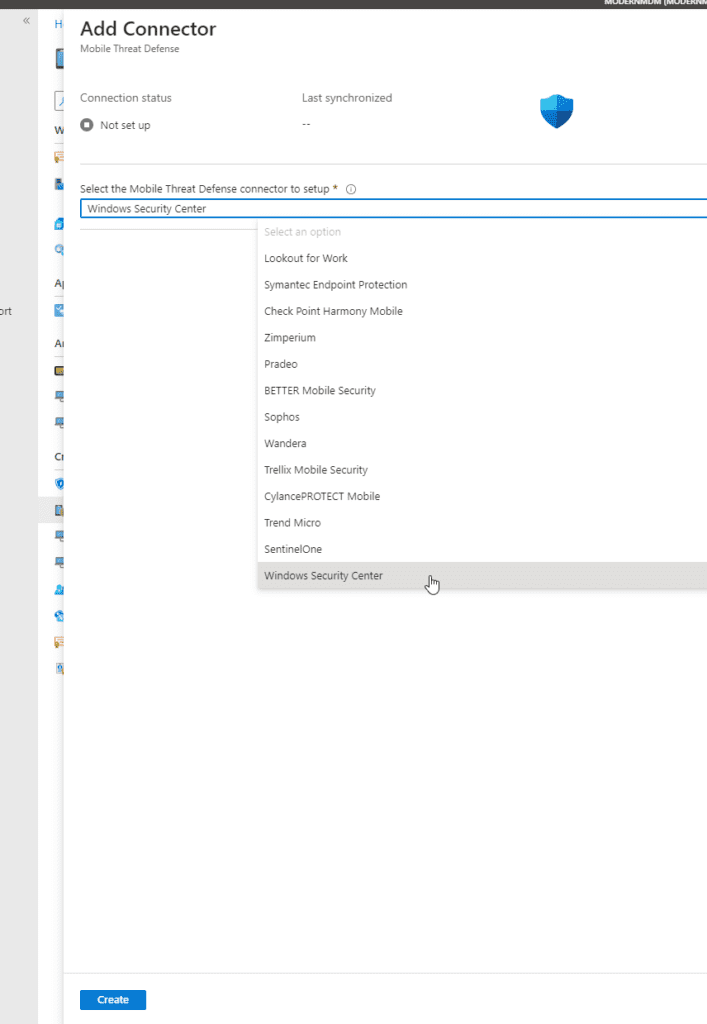
Select the Windows Security Center as the mobile threat defense connector and click create.
Step 3: Create an App Protection Policy for Windows
Go to the Intune Admin Center > click on Apps > App protection policies > + Create policy > Windows App Protection Policy.
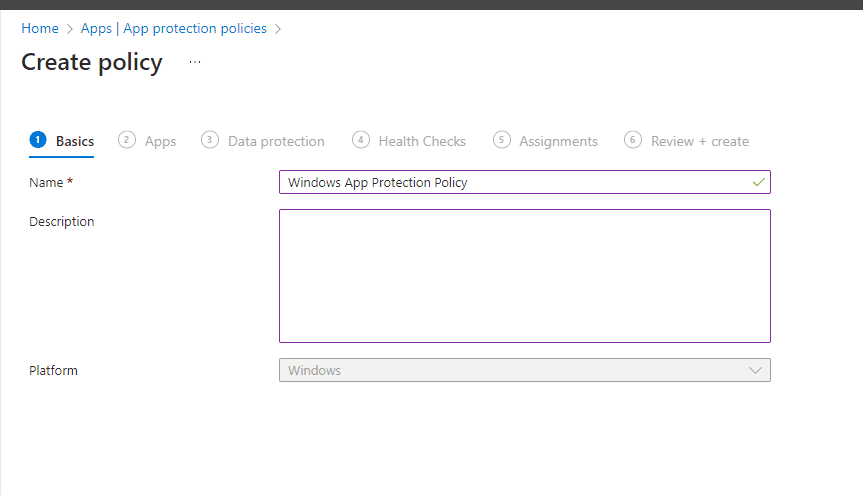
On the Create policy page, name your policy and provide a description for clarity > click Next.
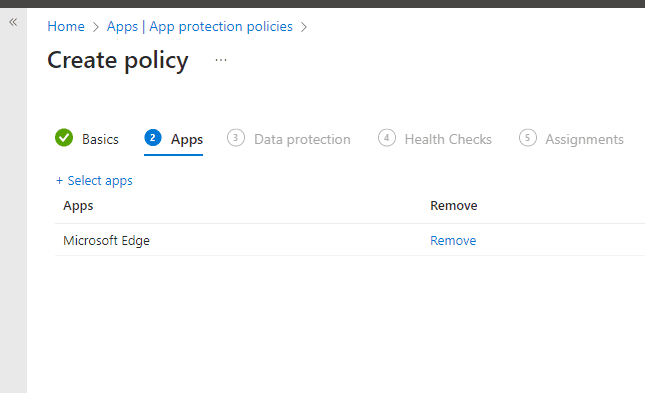
On the next page, click + Select apps and we will target it to Microsoft Edge > Click Next.
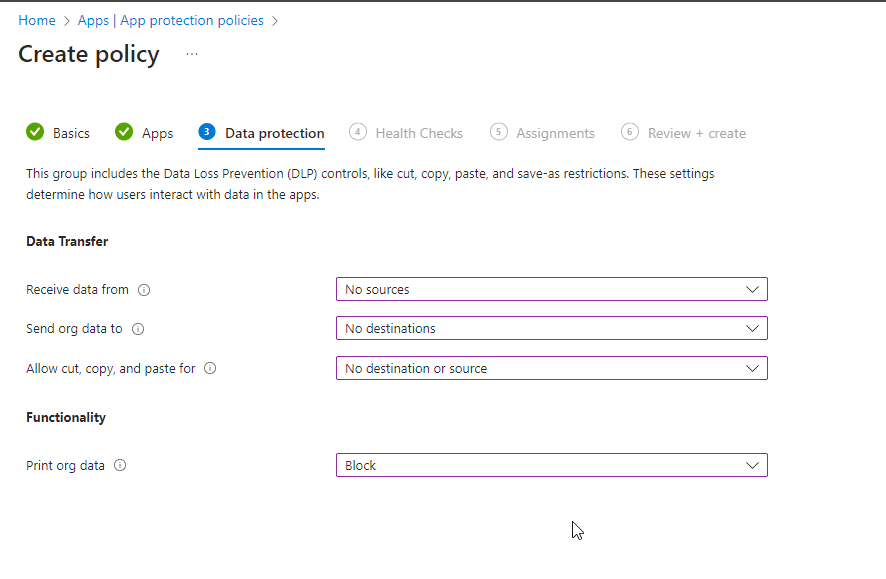
Next, let’s set up the data protection settings, where we can set rules for the application. In the Data Transfer column, we have three settings:
- Receive data from: Your options are All sources and No sources to set where users can receive data from to your application.
- Send org data to: Your options are All destinations or No destination, here you set where users can send org data to.
- Allow cut, copy, and paste for: Your options are Any destination and any source or No destination or source.
Lastly, under functionality you can set to block or allow printing. Print org data: Options are Allow or Block.
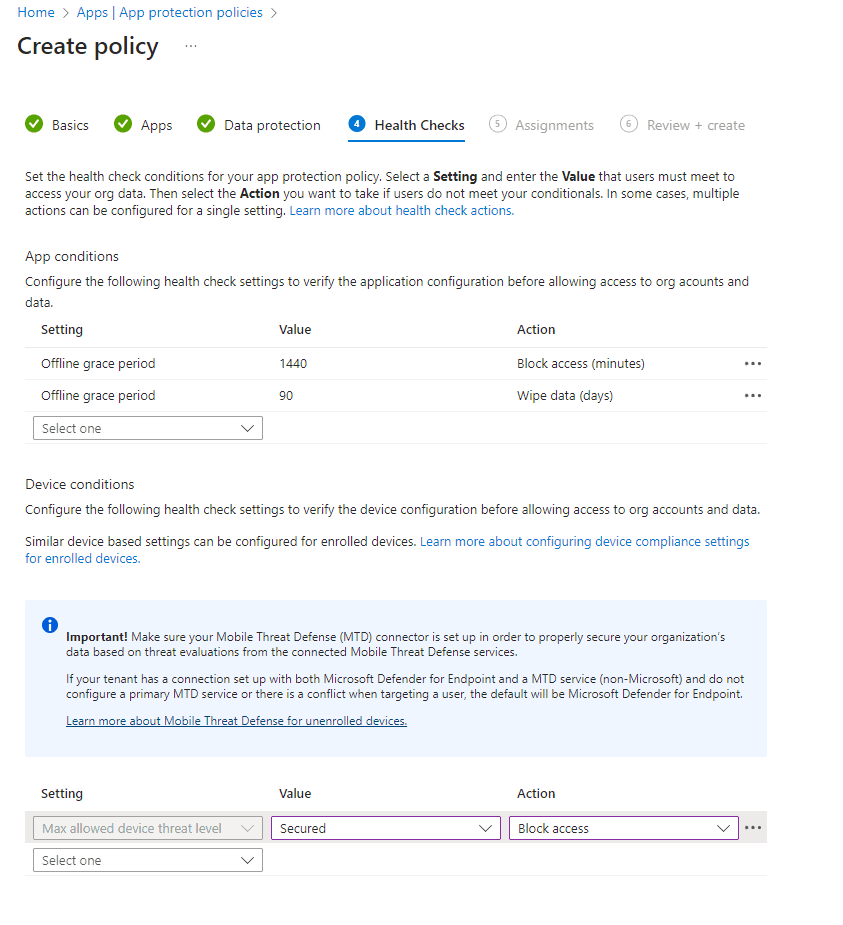
Next move to the Health Checks sections to set app conditions, such as how long an app can be offline before the app protection policy acts.
Also check device conditions such as minimum operating systems or max allowed device threat level to make sure your device is in a secure state before accessing org data. I have kept the defaults but set Max allowed device threat level to the standard value.
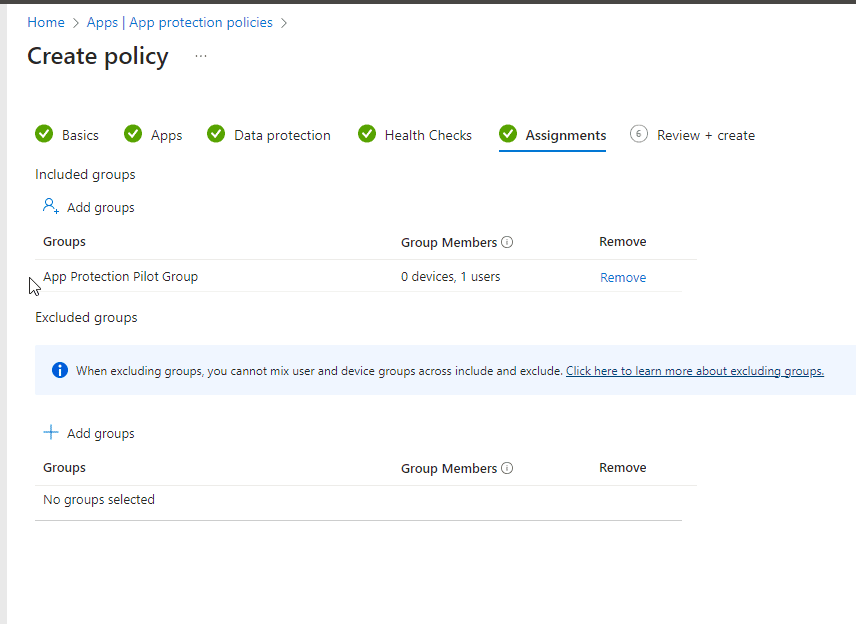
I will also target the same group that I used for the Conditional access policy created earlier, App Protection Pilot Group > Click Next.
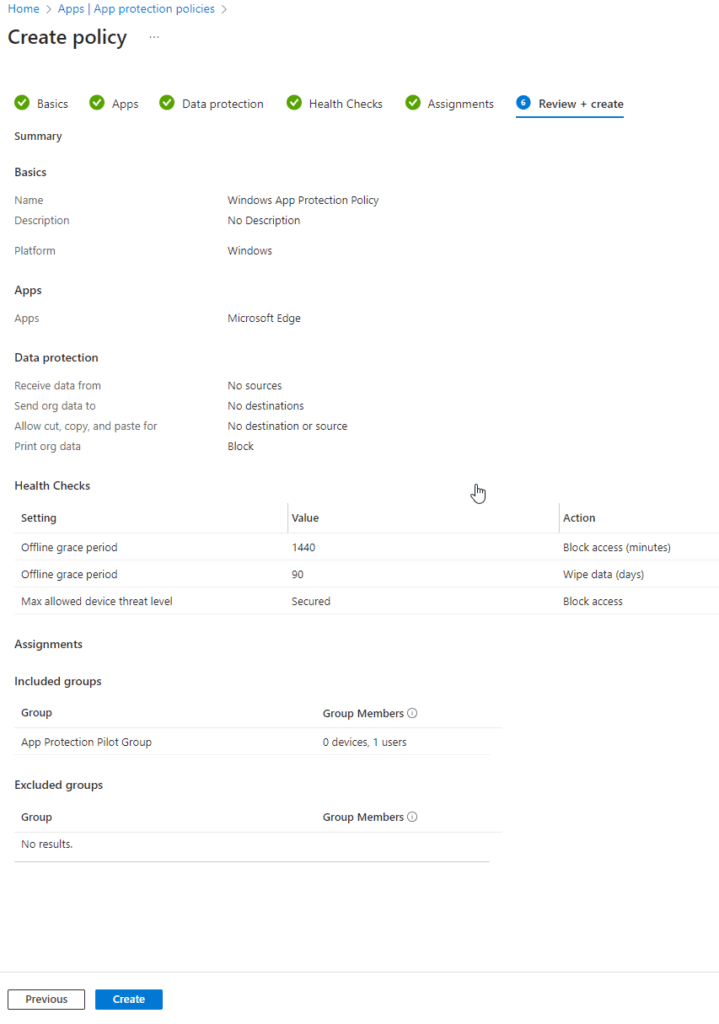
Time to Test
Now that we have our policies set, let’s test them out.
I will try to access portal.office.com from an unmanaged device with Firefox browser. As you can see, I get the following message, which is letting me know I must use Microsoft Edge to access portal.office.com.
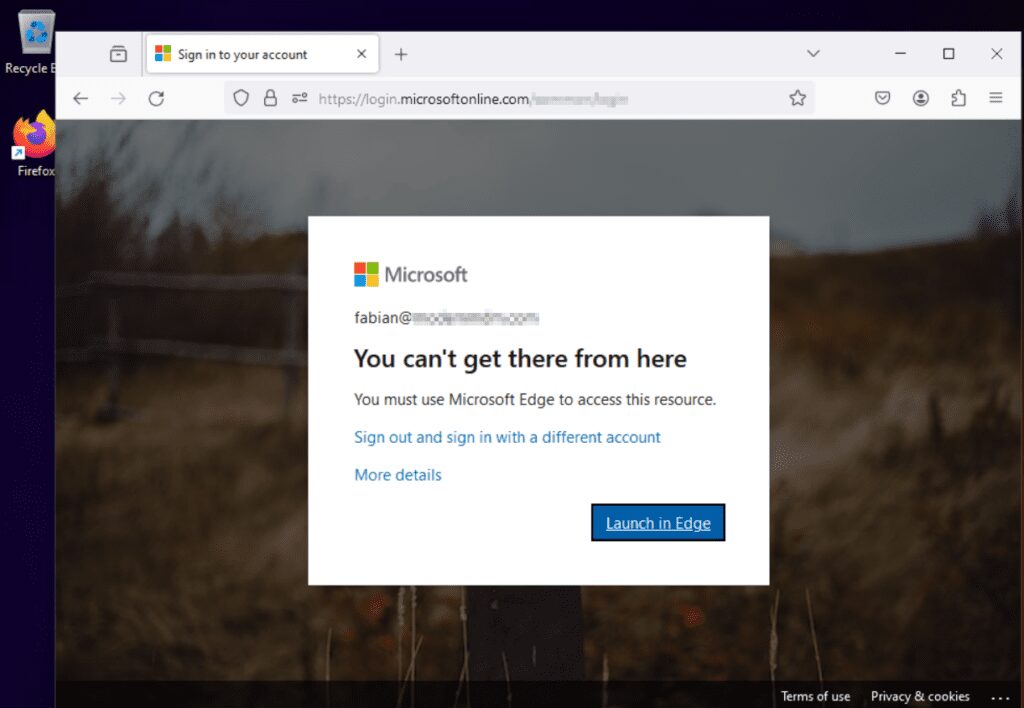
Once I click on Launch in Edge, I am prompted with the following screen (below).
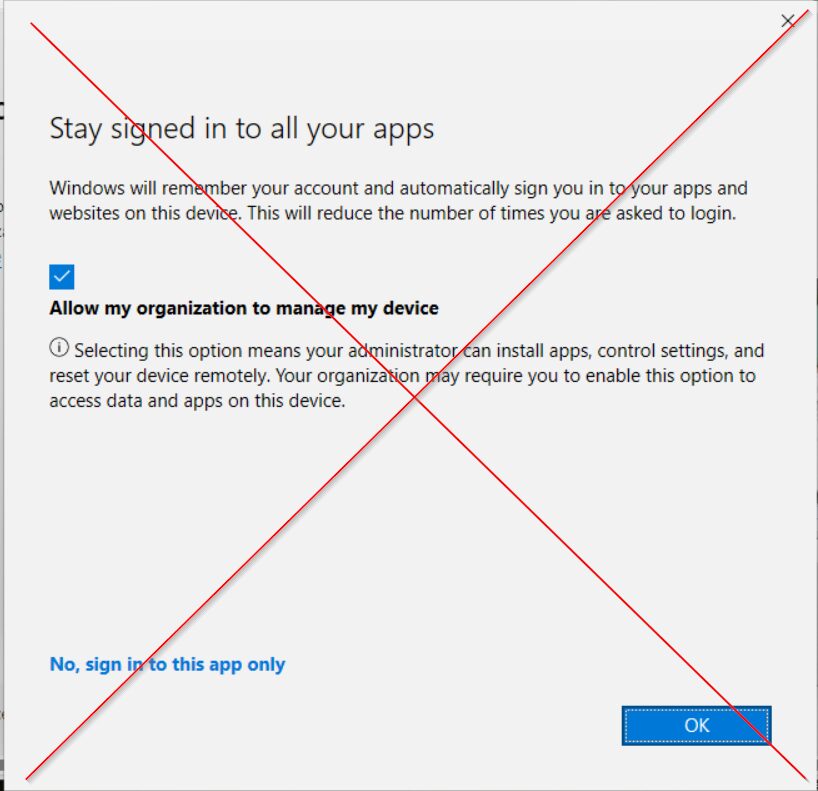
IMPORTANT: Don’t keep the defaults and press OK, as this default setting will register the device and enroll in Intune.
DON’T
DO
Do uncheck the Allow my organization to manage my device and then click ok to register device with Entra AD.
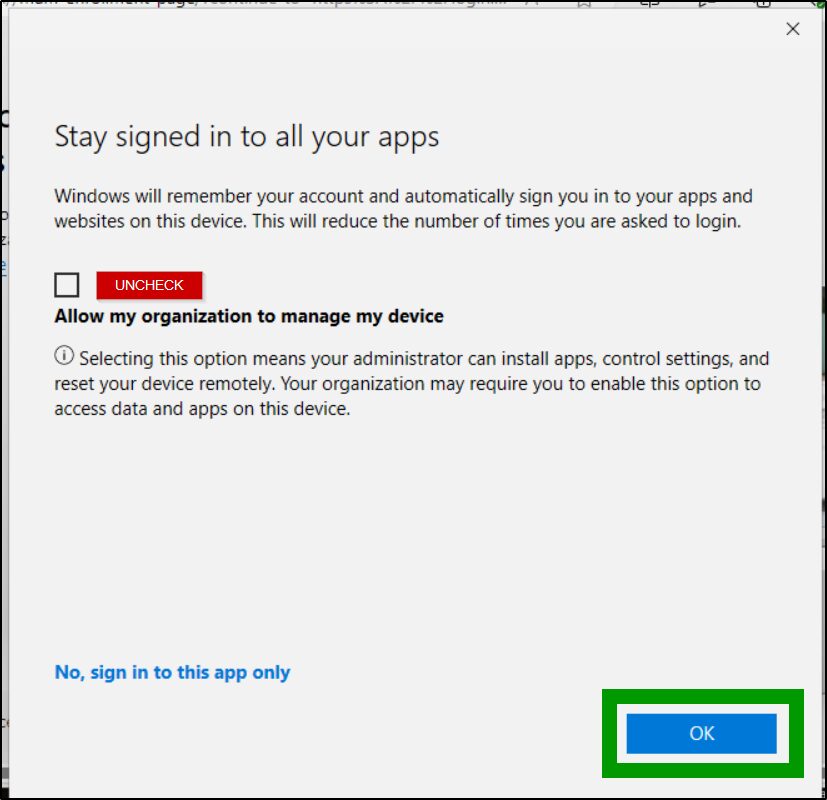
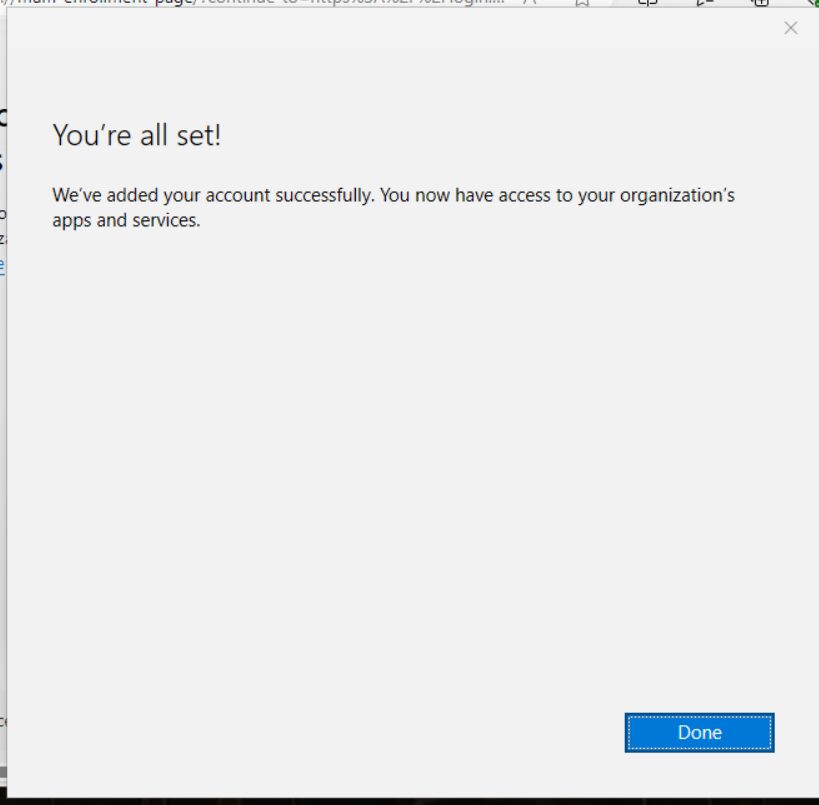
After clicking Ok, I am now able to access my orgs apps and services from Edge on an unmanaged device. Success!
My account is now logged in via my work profile and I can also access Office 365 resources. Check and check.
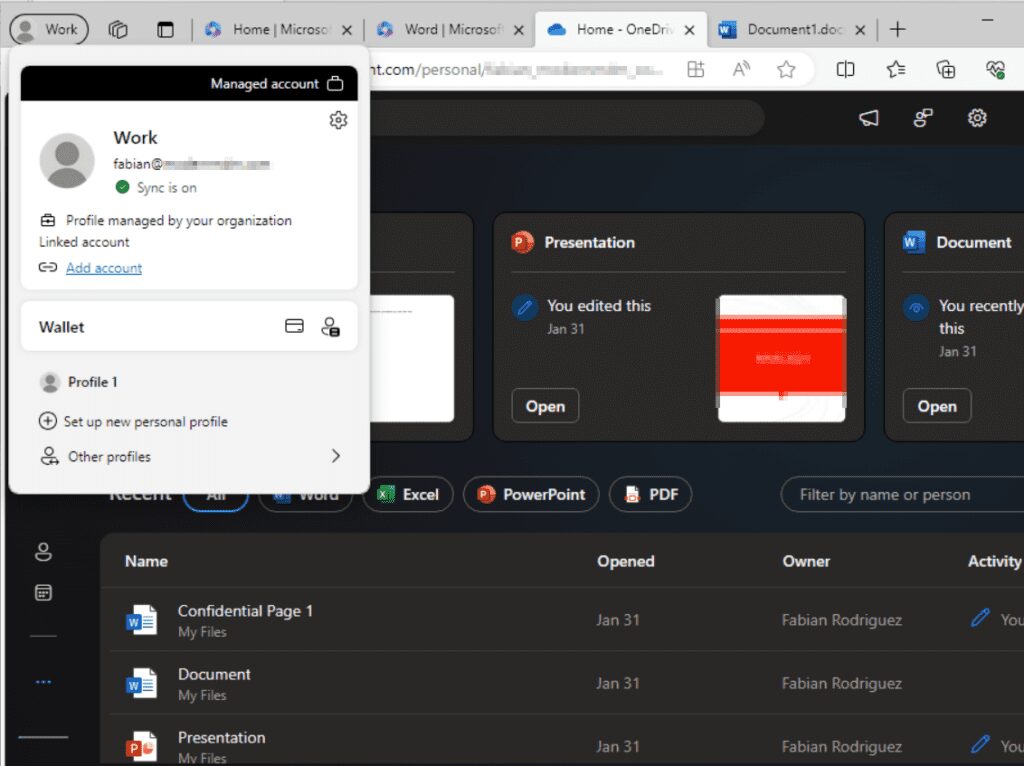
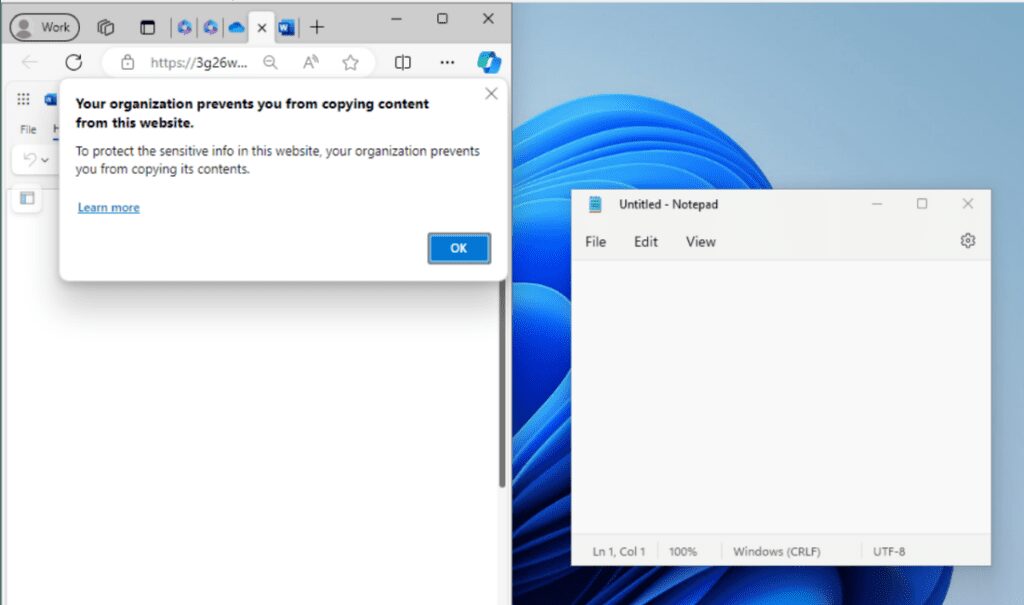
Also notice that I can’t copy data from a Word Document to my personal Notepad, which helps prevent data leaks.
Activated: Mobile Application Management (MAM) for Windows with Intune
Implementing Mobile Application Management (MAM) for Windows with Intune offers a helpful tool for organizations seeking to enhance security without compromising on flexibility. By following the outlined steps to set up MAM, administrators can ensure that unmanaged devices access company resources securely, mitigating the risk of data leaks while accommodating the modern workforce’s needs. This approach not only streamlines application management across devices but also reinforces your organization’s cybersecurity stance.
Additional Intune Posts
- How to Migrate Group Policy Objects to Microsoft Intune
- How to create a Win32 application and deploy with Intune
- How to Set Up Free Microsoft 365 Developer Program
- Collecting Custom Inventory with Intune: A Step-by-Step Guide
- Configure BitLocker on Windows Devices with Intune
- How to Upgrade Windows 10 Devices to Windows 11 with Intune
- Step-by-Step Guide: Enabling Windows LAPS in Entra ID
- How to Configure Bitlocker with Intune
- How to Set Up Windows LAPS with Microsoft Intune