Endpoint Insights
The Four Files You Need to Remove from ConfigMgr Environment – Testing the Baseline Manually
Topics: Endpoint Insights
The Four Files You Need to Remove from ConfigMgr Environment
How to Test the Configuration Baseline Manually
Recently Dana Epp gave a presentation on how hackers can gain access to your environment and how ConfigMgr administrators can reduce these threats. To help get the word out, I promised Dana that I would write this blog post series, but to get more insight make sure to follow Dana on Twitter.
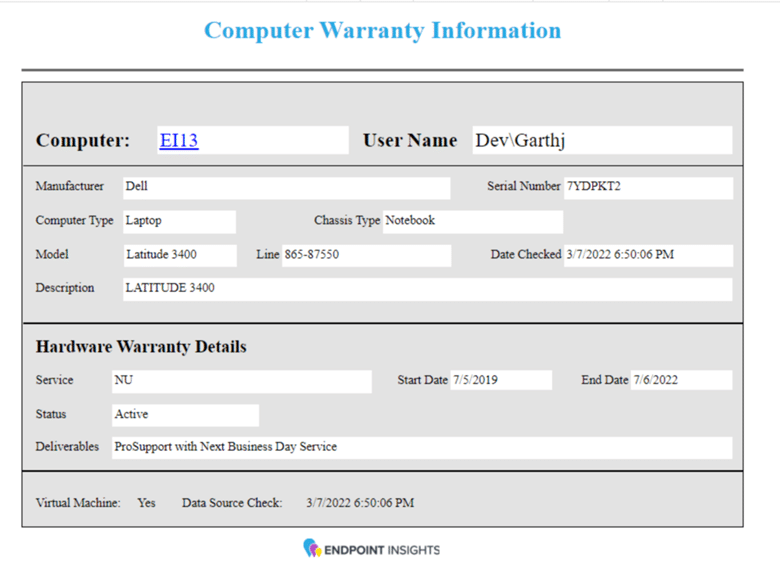
In my previous blog posts about how to remove four specific files in order to reduce your environment’s vulnerability to outside threats, I showed you how to create a Configuration Item, a Configuration Baseline, and how to deploy this Configuration Baseline to all PCs.
If you are impatient like me and do not want to wait for the results from deploying the Configuration Baseline, you can test this Baseline on your local computer. I do this often for troubleshooting purposes.
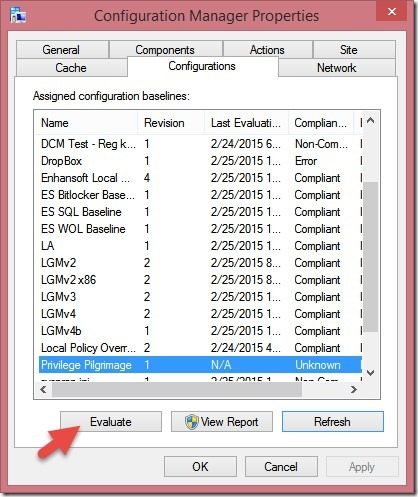
1. On your local computer open Control PanelSystem and Security and double click the Configuration Manager applet. Then click the Configurations tab. Highlight your Configuration Baseline (in this example it is called, Privilege Pilgrimage) and click Evaluate.
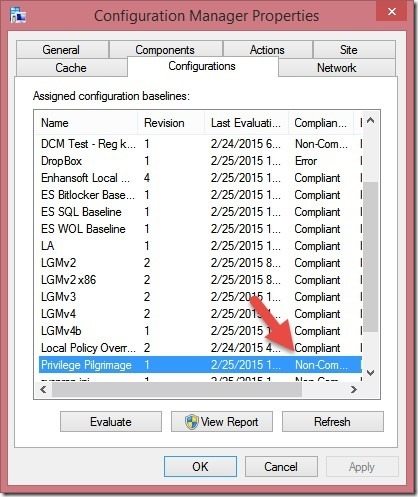
2. Notice that the Configuration Baseline is Non-Compliant. Click View Report to see the details.
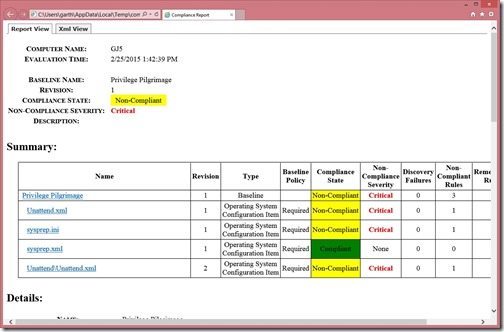
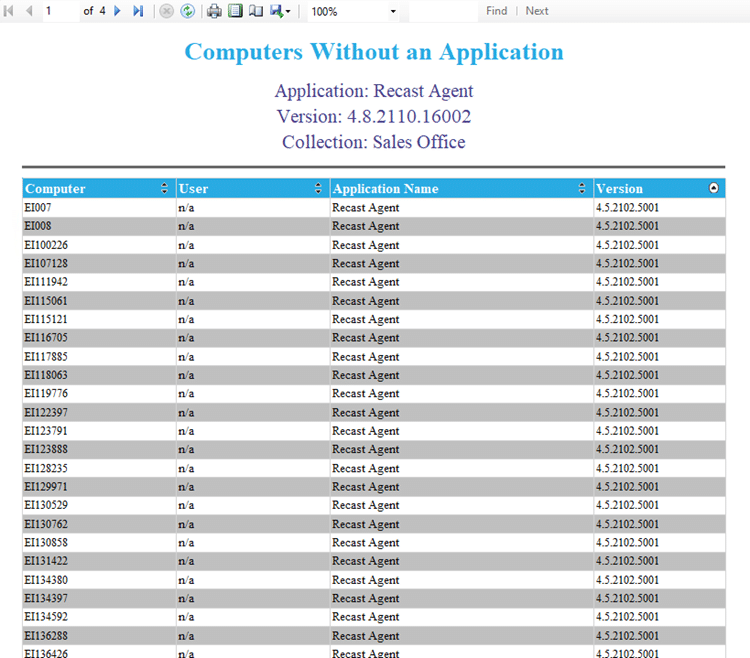
3. Notice that on this PC, three of the four Configuration Items are Non-Compliant.
Since I’m already on this PC, I will manually delete the 3 non-compliant files, and re-run the Evaluation cycle again.
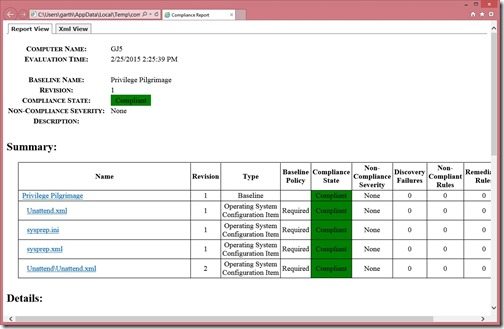
This PC is now compliant. However, if I were to use this method to ensure that every computer was compliant, it would take a very, very long time.
I briefly touched on this in my previous blog post, so instead of checking each PC individually you should send a deployment to all non-compliant computers to delete these troublesome files automatically.
Create the Configuration Baseline Series
- Four Files You Need to Remove from ConfigMgr Environment
- Four Files You Need to Remove from ConfigMgr Environment Baseline