Endpoint Insights
How to Perform a Software Update Audit
Topics: Endpoint Insights
I’m always interested in hearing how people perform a software update audit. Here’s one of the requests I typically see posted within the Microsoft TechNet Forums:
I need a report with Computer Name, User name, Software Updates (SU), and SU status for every computer within my environment.
This is one of those report requests that is generally made for a SU audit. The problem with this type of report is the enormity of data being requested. There is no possible way, due to the sheer volume of information, that you could ever validate all computer data as 100% accurate. In this case, no sooner would you begin your audit when the results would change. It’s a moving target.
What should you do to perform a software update audit?
· First, stop worrying about what is installed on every computer.
· Second, create policy documents.
· Third, create process documents and test plans.
Let’s take a closer look.
On your reporting site, locate the Software Updates – A Compliance folder and execute the Compliance 5 – Specific computer report for your computer. Once the report is executed, export the results to Excel.
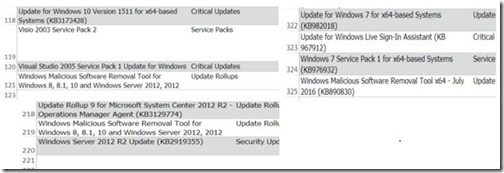
Open the Excel file to see the approximate number of rows for that computer, scroll to the last line within the Excel spreadsheet. Once you have the number of rows, subtract 6, to remove the header rows from your numbers. I’m going to use the following three examples: Windows 10 (121-6) 115, Windows 7 (325-6) = 319, and Windows Server 2012 (221 -6) = 215.
Taking those numbers you can clearly see that if you have 100 Windows 7 computers, you would have 319*100 = 31,900 rows for all the SUs. This is only for 100 computers. Now to put this into perspective, let’s say there are 80 lines on a piece of paper, so 31,900 rows/80 lines = 399 pages of text!
Who will ever read this? No one! This request is unrealistic.
Now let’s turn our attention to the definition of the word audit. Wikipedia states:
Due to constraints, an audit seeks to provide only reasonable assurance that the statements are free from material error. Hence, statistical sampling is often adopted in audits.
Note that this statement says, “…statistical sampling is often adopted in audits.” In all but the tiniest companies, statistical sampling is always used. Auditing the corporate books is no different than auditing the software update compliance.
Getting back to performing a software update audit:
The first step, stop worrying about what is installed on every computer, is easy.
The second step, create policy documents, is also fairly easy to do. It may, however, take some time to write the policy documents for your organization and get them approved by management.
Step 2 – Policies
Without policy documents there is little point to apply software updates (SUs) to your computers. Without them who will know what to apply, when to apply SUs and who is responsible for testing SUs or deploying SUs? It gets worse if there is a problem and no policies are in place. Who can stop the deployment from happening or over-rule the person requesting the SUs to be stopped?
Here are some policy documents you should have, as well as some tasks you should perform:
- Create/review a SU deployment process (Normal).
- Create/review end user notifications (email templates).
- Create/review high level SU testing procedures.
- Create/review a SU deployment process (Emergency).
- Create/review end user notifications (email templates).
- Create/review high-level SU testing procedures.
Tip: The emergency process should be exactly the same as the normal process, but the schedule will be compressed to a significantly shorter time frame.
- Create/review computer/server decommissioning process.
- Remove computer from Active Directory (AD).
- Remove computer from ConfigMgr.
- Remove computer from any Configuration management database (CMDB) or asset management system.
In order to validate that you are following the policies you need to create a reporting process. Below are some of the items you should create:
- Automate reporting.
- Create/review SU dashboards.
- Configure automated report subscriptions.
- Create test plans or check lists to document that each item has taken place within the allotted time frame.
Step 3 – Processes
Now that the policy documents are in place, document the monthly or quarterly process to ensure that software updates are applied in a timely manner. Now it’s time to work on the test plans and check lists that you will need.
Client Health:
- Create test plans or check lists to document that each process step has taken place.
- Ensure all computers have the ConfigMgr client installed.
- Ensure overall health of ConfigMgr clients through:
- Inventory data
- Discovery data
- AV data
- Software updates
- Resolve any computers listed as unknown for SUs.
- Ensure that Active Directory is healthy.
- Ensure that DNS is healthy.
- Ensure that the AV environment is healthy.
- Ensure that ConfigMgr is healthy by examining:
- Management Points
- Software Update Points
- Distribution Points
- Reporting Points
- Review your list of computers missing the most SUs.
- Considering re-imaging any computer with too many outstanding SUs.
- Review/update the list of computers exempted from SUs.
- Create/review SU maintenance windows.
- Question why all SUs have NOT been deployed to all computers.
- Consider implementing Wake-On-LAN (WOL) for SU deployment.
- On a monthly basis, review your overall compliance rate and record your progress over time.
Remember that a few of these things will affect your overall compliance rate. For example, by ensuring that your computer decommissioning process is followed, you will increase your SU compliancy by removing computers that are no longer active within ConfigMgr. Using WOL will allow you to apply SUs off-hours to all computers without the need for manual intervention. This will increase your compliancy rates too.
Working on these steps will help ensure that SUs are applied in a timely manner and that your overall compliance will increase. By recording your progress over time you can see if you are getting better or worse. This last task alone will help allow you to justify the need for more or less staff.
How can we help you with this? We produce a number of dashboards and reports that will allow you to see your overall SU compliance in a consistent manner. This will allow you to record the results to demonstrate the overall effectiveness of SU deployment strategies.
For example, Endpoint Insight’s Most Vulnerable Computers Online dashboard (see below) is an excellent report for the Service Desk to use. It allows them to see the computers that require the most attention that are currently online. This report allows administrators to focus their remediation efforts on active computers.
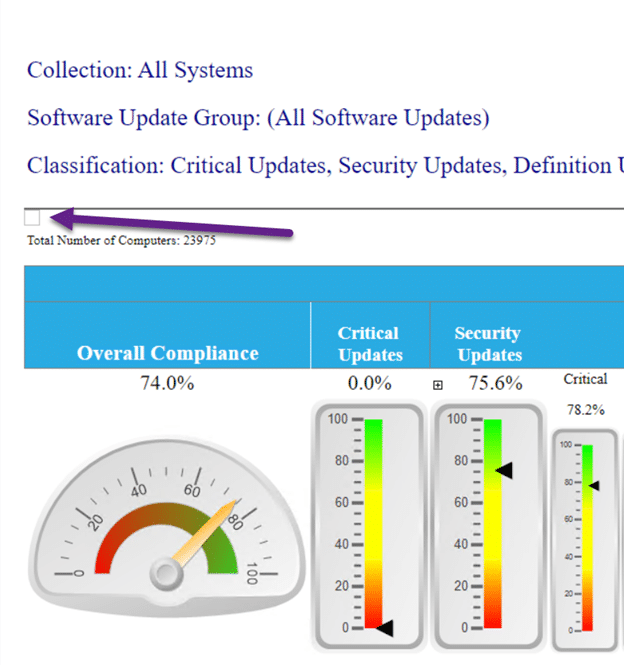
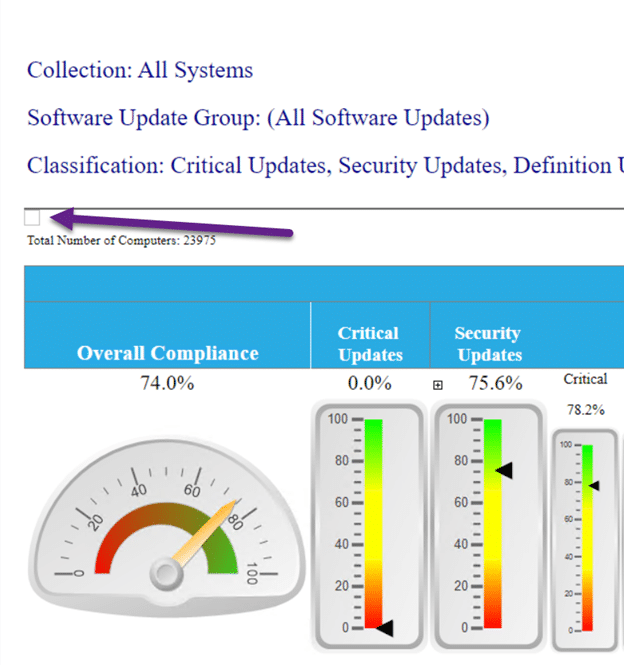
The Overall Missing Software Update Status by Classification dashboard, also in Endpoint Insights, (see below) is great for the security team as it shows them, at-a-glance, what percentage of all SUs have been applied to the environment and if there are any concerns that require future investigation.


Software Update Audit Conclusion
If you have any questions about a software update audit, simply drop me a line at @GarthMJ, and you can learn more about Endpoint Insights here.